Reverse Deception: Organized Cyber Threat Counter-Exploitation (88 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

BOOK: Reverse Deception: Organized Cyber Threat Counter-Exploitation
9.12Mb size Format: txt, pdf, ePub
You need to take one step beyond the mindset of employing preventative host-based IDSs and IPSs. One small avenue of approach is all your adversaries need to find. It’s better to proactively find it yourself before they can.
Table 8-6
lists some of the tools that can assist in these efforts. There are free and paid versions of each tool.
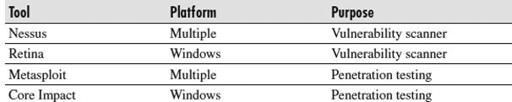
Table 8-6
Host/Server Vulnerability Testing Tools
These tools work as follows:
Nessus
Professionals have used this popular, proven tool for years. It scans specified hosts on a network and provides a detailed report on the vulnerabilities on those hosts. You can use it at home to scan a limited number of IP addresses for free, or purchase the paid version for commercial use. You can find it at
www.tenable.com/
.
Retina
This is a Windows-based vulnerability scanner, which also allows you to see the hosts on your network that could compromise your overall security. Retina offers a free version for limited use or commercial versions to check your full network. You can download it from
www.eeye.com/
.
Metasploit
This is a powerful, multiplatform penetration testing tool that provides an easy-to-use environment you can use to attempt to exploit any vulnerabilities you discover on your hosts. This is truly a proactive way for you to find out how an attacker can compromise your systems and security.
Figure 8-10
shows an example of Metasploit in use. For more information, or to download the free or paid version, visit
www.metasploit.com/
.
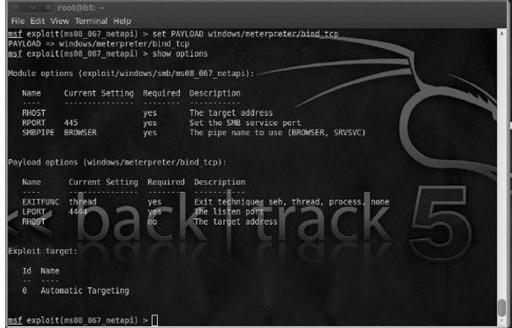
Figure 8-10
Check yourself with Metasploit
Core Impact
This is a comprehensive, Windows-based penetration testing tool that allows the wielder to attempt a wide range of possible threats against your network. The best way for you to find out how your systems can be exploited is to use a tool such as this. For more information, visit
www.coresecurity.com/
.
What Are You Looking For?
Check the following:
What did the chosen application report as a flaw in your host or network?
How did it get there?
How can you fix it?
Do you recognize all the devices with flaws as being authorized for use on your network?
How can you fix these flaws on the hosts?
Do you recognize the web-based applications possibly running on those hosts or servers?
Other books
Avengers of the New World: The Story of the Haitian Revolution by Laurent Dubois
The Detective Inspectors (The Doorknob Society Saga Book 4) by Fletcher, MJ
Cold Coffin by Nancy Buckingham
Escuela de malhechores by Mark Walden
The Silk Merchant's Daughter by Dinah Jefferies
The Kinky Side Scrooge of Scrooge by Cane, Veronica
Dragons' Onyx by Richard S. Tuttle
The Whispering: A Haunted House Mystery by Sarah Rayne
Zombies: The Recent Dead by Paula Guran
