Reverse Deception: Organized Cyber Threat Counter-Exploitation (86 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

How Does Your Wireless Network Look?
You would be hard-pressed to find a company today that doesn’t have some type of wireless network. It’s cheaper than running cables to each workstation and easily allows for the addition of devices, all reducing the overall maintenance cost and overhead. However, if not configured properly, these wireless devices can leave a gaping hole in your network. In addition, if not careful, your business could find itself hosting one or more rogue access points, meaning that someone has placed an unauthorized wireless access point on your network. Don’t discount the usefulness of a wireless network, but make sure you test its security.
Table 8-4
lists some free tools that can help you in this effort.
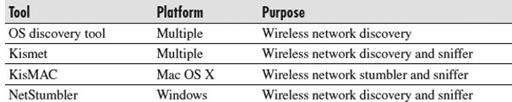
Table 8-4
Free Wireless Network Discovery Tools
These tools work as follows:
OS discovery tool
This is the wireless network tool included with your operating system of choice. Some versions have limitations, such as failure to discover wireless networks that do not broadcast their SSID, so you may choose to use other tools.
Kismet
This is a console-based passive network discovery tool and sniffer that does not suffer from some of the limitations of your operating system’s network discovery tool. You can learn more about this tool and download it from
www.kismetwireless.net/
.
KisMAC
This is a GUI-based wireless network discovery tool that also offers the capability to crack wireless encryption keys, which is another bonus in determining your wireless security posture.
Figure 8-8
shows an example of KisMAC in action. You can find this tool at
http://kismac-ng.org/
.
Figure 8-8
KisMAC in action
NetStumbler
This is a Windows-based tool used for discovering wireless access points. The author of the tool is supposedly working on updating the code so that it will work on Windows Vista and Windows 7. For more information or to download the tool, head over to
www.stumbler.net/
.
What Are You Looking for?
Check the following:
Do you have wireless routers/access points connected to your network?
Are the wireless routers/access points discovered during your scan authorized to be on your network?
How are the configurations of the routers/access points authorized to be on your network?
Do they have administrative passwords set?
Are they using the appropriate level of encryption?
Has the default SSID been changed?
