Reverse Deception: Organized Cyber Threat Counter-Exploitation (87 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Are you broadcasting the SSID?
Are the latest firmware patches applied to the wireless device?
What’s Traveling on Your Network?
Whether your network is large or small, you likely have a lot of traffic entering and leaving it each and every day. While you are probably reluctant to believe any people you work with would maliciously transmit anything they shouldn’t, you don’t know unless you are an active participant in your network security. Plus, without checking, you may not know until it is too late that one of your coworkers mistakenly clicked on that malware-laden PDF, which caused one or more machines on your network to be recruited into a botnet. Keeping up with all the traffic on your network is a daunting task, but it is a necessary evil about which you must be diligent. Some of the tools listed in
Table 8-5
, which are available at no cost, may help you in this endeavor.
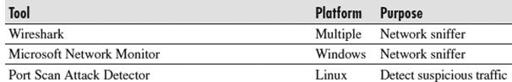
Table 8-5
Free Traffic Capture Tools
These tools work as follows:
Wireshark
This is one of the most widely used tools to capture traffic on your network. It allows you to view traffic in real time, as shown in the example in
Figure 8-9
. Find out more and download it at
www.wireshark.org/
.
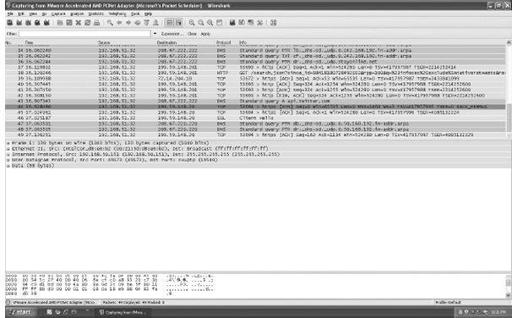
Figure 8-9
Packet capturing with Wireshark
Microsoft Network Monitor
This is a tool developed and distributed by Microsoft for Windows platforms that allows the capture and analysis of traffic on your network. You can find it at
www.microsoft.com/download/en/details.aspx?displaylang=en&id=4865
.
Port Scan Attack Detector
This Linux-based tool is used to analyze specific network traffic logs to determine if any hosts on your network are being port-scanned, as well as search for other suspicious traffic. It ties in nicely with some visualization tools, giving you the ability to graphically view the traffic flow to and from some of your hosts. You can find this tool at
http://cipherdyne.org/psad/
.
What Are You Looking For?
Check the following:
Are there any machines on your network displaying an unusual amount of traffic flow?
Are any machines on your network receiving or transmitting packets on ports outside the norm?
Are your machines running services that they are not authorized to run?
Do any of your machines communicate with a number of machines outside the local network, especially during nonworking hours?
What About Your Host/Server Security?
Testing the security of the hosts on your network is absolutely critical to ensure that your friendly hacker doesn’t find them for you. Patches are released frequently from multiple application and operating system vendors, and depending on your manpower to adequately push all of these patches, you may find yourself at risk.
What’s more important is that patches are not the panacea of host/server security. They may wind up modifying the security configuration you had to lock down your machines. In addition, unless you have the proper mechanisms in place, do you really know if the patches have made any changes that compromise the security of your network?
