Reverse Deception: Organized Cyber Threat Counter-Exploitation (90 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Do your system accounts have the appropriate restrictions applied?
How’s Your Operational Security?
Well, you’ve made it this far. You are taking all the appropriate measures to protect your systems from compromise, but is it all for naught?
Many of your common and advanced threat actors begin their work by performing reconnaissance on you, your coworkers, your employees, and your company. They will learn as much about your company as possible in order to maximize their chances of success and reduce their risk of getting caught. What better way to gather intelligence on their target than to see what you or those who you work with post online? It’s not only the data contained within the documents that could do you harm, but the hidden data (such as metadata) that can reveal information about your network to the attacker.
One of the tools that can help you find out if you are your own worst enemy is FOCA. You simply point the program at a domain name, tell it what documents you want to check (such as Microsoft Word .doc files), tell it which files to download, and extract the metadata.
Figures 8-12
and
8-13
illustrate FOCA in use.
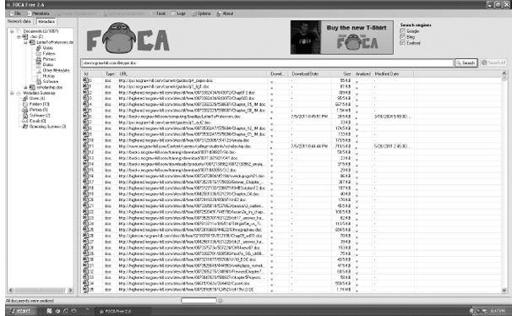
Figure 8-12
Finding publicly accessible documents with FOCA
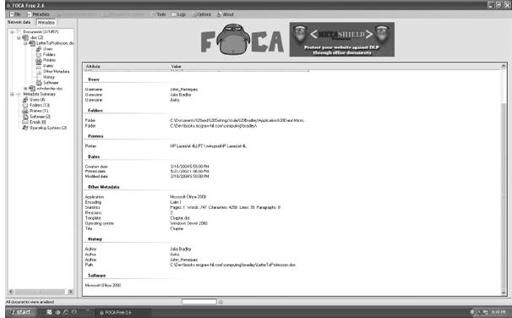
Figure 8-13
Pulling hidden information from documents
What Are You Looking for?
Check the following:
Are any documents posted that reveal information about your company that should not be available online for the world to see?
Are there any usernames in the metadata of the document that could reveal the username naming conventions used on your network?
Are there any document paths revealed in the metadata that could help provide a tip-off to the server and machine names located on your network?
Does the metadata in the document reveal any printers used on your network?
Printers are very vulnerable to compromise, as they are most often overlooked in the update and patching process to close any vulnerabilities.
Does the metadata reveal the operating system used to create the document?
This could provide your attacker very worthwhile information and reduce the chance of failure, since many enterprise networks use the same operating system.

Crimeware/Analysis Detection Systems
So, you’ve applied some of the preventative measures mentioned earlier in the chapter, and you’ve checked your protection on a regular basis as we just discussed, but they still got in. The people you spent so much time protecting yourself against were able to breach your defenses, muck with your best-laid plans, and take your valued information. Well, that is the nature of the beast. It happens, and it will probably happen again. What comes next and how you learn from the incident will help define the future state of your security.
To really learn from what has happened, you should take some time to evaluate the incident, study the tools used by your attackers to find out how they got in, and incorporate these into your lessons learned. In order to do that, you will need to grab some tools commonly used by digital forensic investigators. Here, we’ll provide a short introduction to some of those tools and concepts. The coverage is not exhaustive, as you can find complete books dedicated to these topics, but it will point you in the right direction.
