Reverse Deception: Organized Cyber Threat Counter-Exploitation (114 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Now suppose that the intruders did not access all of your intellectual property regarding one of your company’s high-profile projects. Some might be quick to decide that they took information just because they were able to access it while they were there. However, consider a scenario where they targeted the company and a specific subset of information because that was all they needed. What else about the project could they find on your website or through your favorite search engine? What else have they taken from your partner companies in the project? These questions need to be addressed as well to give you a better picture of why you were targeted in this attack.
As mentioned earlier, your logs will provide you with a lot of the information you need. Study the actions of your intruders. Understand how they operate. Critically look at what they did and how they did it. Some actions they took on the network are probably nothing more than a feint, meant to throw you off their trail. Other actions can provide you with a view into the reason they were there. What we have talked about in this section is only the tip of the iceberg. The concept can be applied in every situation, but every situation cannot be covered.
Responding to Actionable Intelligence
As used here, the term
actionable intelligence
refers to information you have obtained that can help determine what actions you should take against threats. This information will assist you in either protecting your network and information from future attacks or in determining the source and objective of past attacks.
Consider a situation where your sources have provided you with information that another company wants to acquire information related to your latest research and development efforts. You know that you are only a few months away from launching a game-changing product, and if the competitor acquired this information, it would mean ruin for your company. If you wonder if this could ever happen to you, just search for “commercial espionage” in your favorite search engine. Now anyone who has valuable information can make you a target, and you need to know what you are going to do about it. You really have several viable options.
In this day and age of all things cyber, you can hazard a guess that someone may attempt to breach network security to obtain your intellectual property. In this case, you will want to ensure that the security is tight. It’s better to leave nothing to chance. Also, as we have stressed many times in this book, no security is impenetrable. Gunter Ollman, who has spent more than 25 years in penetration testing, once said, “We have always gotten in.”
Consider turning the tables on your foe. If you are aware, you are prepared. Once you build it, they will come. The target’s objective is known, at least to an extent based on its end game. The subtle differences will be the injection vectors/entry points, tools usage, exfiltration techniques, and much more. You have taken measures to increase the protection of your prized and valuable information. What would happen if you placed some information on your network that looked like the real thing, but wasn’t? In this situation, you are the Greeks and they are the Romans in a modern-day version of the Trojan horse.
While we have focused a lot of our effort on actions in the digital realm, do not discount the likelihood that that your competitor will attack the weakest link in your chain: the employees. Attacks against the human element have occurred for centuries, because they have been, and likely will always be, successful. Your competitor could try to recruit one of your employees to provide information, preying on that employee’s need for money, dissatisfaction with his current position, or just because he can. Or you could face a more serious threat: the social engineer. Social engineering is a low-tech method for others to get unauthorized access to information, many times without you knowing that they gained the access. These two situations require management and security personnel to create and sustain a good user awareness program. An educated employee could be your last line of defense against commercial espionage.
All in all, actionable intelligence will help you plot your future course of action. Actionable intelligence is simply information that provides enough context of a series of events to aid the victim organization in developing its overall plan to engage and/or counter the threat using some level of actions. Hence, the word “actionable.”

Cyber Threat Acquisition
Cyber threat acquisition (CTA) is the practice of honing your sensor network specifically in on a precise threat that is actively operating with impunity across your enterprise. The preceding chapters have helped you build a dossier on the threat, and now you need to take some level of action against the threat.
CTA involves the skills of honing in on the precise observables of a specific actor and closing in on the threat from all sides, with enough intelligence that should help improve future detection techniques across your enterprise. Acting at the right time goes back to operating with timeliness against a focus. Continue reading to learn more about distinguishing actions that can help eliminate the threat and strengthen your enterprise security posture.
Distinguishing Between Threats
When you have numerous incidents where multiple systems are infected by unknown actors, how do you distinguish between the different groups? The answer always lies in the network data traversing your enterprise.
One method is performing link analysis on the various CnC servers each infection is communicating with. Another method is to actively engage actors in criminal forums to identify who is running which campaigns and/or using which tools. Some analysts attempt to begin at the host level and work their way up, which has been the standard operating procedure for incident responders for well over a decade. However, as we are all aware, crimeware in and of itself can be armored and packaged to appear as other families of malware and not relinquish any information as to the true tool. Cryptors, packers, and binders can alter and armor the actual bare crimeware agent that is used to pilfer victim systems and send the stolen data out of the network.
When distinguishing between threats, you can start at the host and look for observables based on a malicious sample’s actions. In some samples, you can identify the use of various sandbox technologies. There is also the network perspective, which you can leverage as another component for distinguishing between threats.
Here, we’ll look at some crimeware samples and then examine some of the network data from each of them to identify specific patterns or unique regular expressions we can build to distinguish between each threat.
Example: MD5 of Binary 18eb6c84d31b5d57b3919b3867daa770
We’ll start with a simple example:
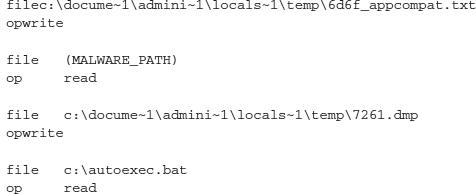
As you can see, this sample performs a minimal set of actions on a host and then executes the following process:
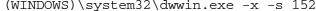
This type of threat is a generic “run-of-the-mill” sample that performs simple actions against a victim’s system.
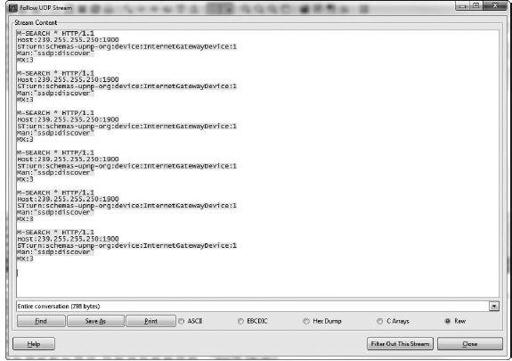
As you can see in the following example, this particular crimeware sample simply performed some specific checks via UDP to a remote IP address on port 1900:
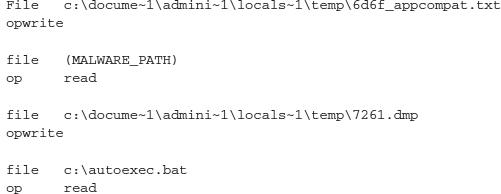
The question presents itself: What are the unique characteristics associated with a variant of a campaign? There are a few observable traits that can be gathered between the host and the network layers. First, we will look at the host-based patterns. Initially, you can see that this sample interacts with a handful of directories, primarily \locals~1\temp\ and C:\.
You can visit
www.Virustotal.com
for more information about the actual executable that was initially loaded onto the victim’s system. The following is some high-level information on the binary itself:
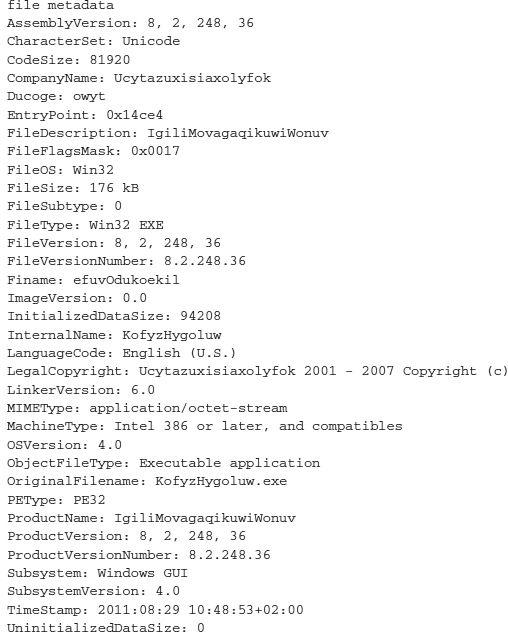
As you can see, the sample was initially compiled on 8/29/2011 and was first processed by VirusTotal on 11/2/2011, which means this has been running around a while. This infers that the operator took some time to set up an infrastructure and then armored the binary some time later.
The overall detections point to a Zeus or SpyEye bot-based infection. This type of campaign can be based on numerous opportunistic and targeted groups. This leads us to the network usage of this executable, which should provide a little more information on the avenue of ingress and egress of the malware. Two different UDP streams are associated with this sample. The first is the initial check-in to a hacked web server that is hosting the botnet collector and is not a part of the victim’s infrastructure, but a completely different victim. The first UDP attempt is trying to connect to the domain
fugue.com
. What can we learn about that domain? Take a look at the first UDP stream: