Windows Server 2008 R2 Unleashed (57 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

SSO a reality, however, with the Identity Management for UNIX role service.
Identity Management for UNIX is an additional role service on a Windows Server 2008 R2
machine that includes three major components, as follows:
.
Server for Network Information Services (SNIS)—
Server for NIS allows a
Windows AD DS environment to integrate directly with a UNIX NIS environment by
exporting NIS domain maps to AD entries. This allows an AD domain controller to
act as the master NIS server.
.
Password Synchronization—
Installing the Password Synchronization role on a
server allows for passwords to be changed once, and to have that change propagated
to both the UNIX and AD DS environment.
.
Administrative Tools—
Installing this role service gives administrators the tools
necessary to administer the SNIS and Password Synchronization components.
The Identity Management for UNIX components have some other important prerequisites
and limitations that must be taken into account before considering them for use in an
environment. These factors include the following:
. Server for Network Information Services (SNIS) must be installed on an Active
ptg
Directory domain controller. In addition, all domain controllers in the domain must
be running Server for NIS.
. SNIS must not be subservient to a UNIX NIS server—it can only be subservient to
another Windows-based server running Server for NIS. This requirement can be a
politically sensitive one and should be broached carefully, as some UNIX administra-
tors will be hesitant to make the Windows-based NIS the primary NIS server.
. The SNIS authentication component must be installed on all domain controllers in
the domain in which security credentials will be utilized.
Installing Identity Management for UNIX Components
To install one or all of the Identity Management for UNIX components on a Windows
Server 2008 R2 server, perform the following steps from a domain controller:
1. Open Server Manager (Start, All Programs, Administrative Tools, Server Manager).
2. Expand the Roles node in the tasks pane, and select Active Directory Domain Services.
3. Right-click the Active Directory Domain Services role, and select Add Role Services.
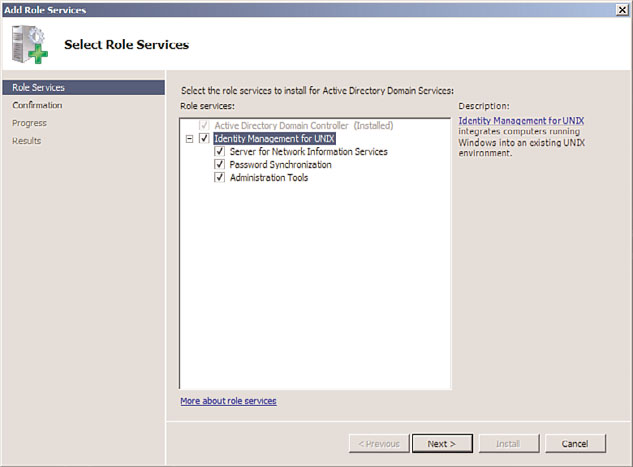
Check the box next to Identity Management for UNIX, which should automatically
check the remaining boxes as well, as shown in Figure 9.5. Click Next to continue.
4. Review the installation options, and click Install to begin the process.
5. Click Close when complete, and choose Yes to restart the server.
6. After restart, the server should continue with the configuration of the server before
allowing you to log on. Let it finish and click Close when the process is complete.
Understanding the Identity Management for UNIX Components
255
FIGURE 9.5
Installing the Identity Management for UNIX components.
ptg
Configuring Password Change Capabilities
To enable password change functionality, a connection to a UNIX server must be enabled.
To set up this connection, perform the following steps:
1. Open the MMC Admin console (Start, All Programs, Microsoft Identity Management
for UNIX, Microsoft Identity Management for UNIX).
2. In the node pane, navigate to Password Synchronization, UNIX-Based Computers.
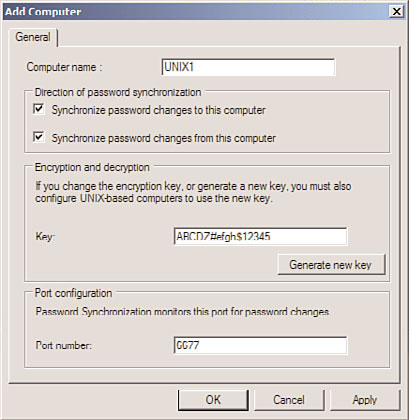
3. Right-click on UNIX-based Computers, and choose Add Computer.
4. Enter a name in the Computer Name text box, and specify whether to sync pass-
words to/from UNIX. Enter the port required for password sync and an encryption
key that is mutually agreed upon by the UNIX server, similar to what is shown in
Figure 9.6. Click OK.
9
5. Click OK to confirm the addition of the UNIX system.
Adding NIS Users to Active Directory
For users who want their existing NIS servers to continue to provide authentication for
UNIX and Linux servers, the SNIS component might not be the best choice. Instead, there
is a package of Korn shell scripts downloadable from Microsoft.com that simplifies adding
existing NIS users to AD. The getusers.ksh script retrieves a list of all users in a NIS data-
base, including the comment field. This script must be run with an account with the
permission to run ypcat passwd. The makeusers.ksh script imports these users to Active
Directory. The makeusers.ksh script must be run by a user with domain admin privileges.
The –e flag enables accounts—by default, the accounts are created in a disabled state. This
256
CHAPTER 9
Integrating Active Directory in a UNIX Environment
FIGURE 9.6
Configuring password sync to UNIX systems.
is a perfect solution for migrations that will require the existing NIS servers to remain
ptg
intact indefinitely.
NOTE
For more advanced scenarios that involve automatic synchronization between UNIX NIS
accounts and AD DS user accounts, including automatic provisioning/deprovisioning
and attribute synchronization, consider using the Forefront Identity Manager (FIM) prod-
uct from Microsoft. FIM’s predecessor, ILM 2007, is covered in more detail in Chapter
8, “Creating Federated Forests and Lightweight Directories.”
Administrative Improvements with Windows Server
One of the main focuses of Windows Server 2008 R2 UNIX Integration was the ability to
gain a better measure of centralized control over multiple environments. Tools such as an
enhanced Telnet server and client, ActivePerl 5.6 for scripting, and a centralized MMC
Admin console make the administration of the Windows Server 2008 R2 UNIX
Integration components easier than ever. Combined with the improved MMC interface in
Windows Server 2008 R2, it is easier than ever to manage mixed environments from the
Windows platform.
Performing Remote Administration with Telnet Server and Client
Windows Server 2008 R2 UNIX Integration uses a single Telnet service to provide for
Telnet functionality to both Windows and UNIX clients. This was a change over the way
Administrative Improvements with Windows Server 2008 R2
257
that it previously was, as two separate components were installed. This version of
Windows Server 2008 R2 Telnet Server supports NT LAN Manager (NTLM) authentication
in addition to the basic logon that supports UNIX users.
To install the Telnet Server component, perform the following steps:
1. Open Server Manager (Start, All Programs, Administrative Tools, Server Manager).
2. Click on the Features node in the tasks pane, and then click the Add Features link.
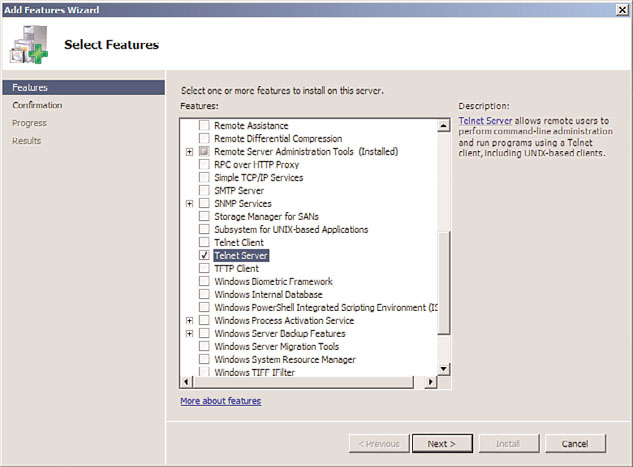
3. Check the box next to the Telnet Server role, as shown in Figure 9.7. Click Next to
continue.
ptg
FIGURE 9.7
Installing the Telnet Server role for UNIX clients.
4. Review the settings and click Install.
9
5. When the wizard is finished, click Close.
Scripting with ActivePerl
With Windows Server 2008 R2 UNIX Integration tools, you can write scripts using the
ActivePerl tool, which was fully ported from UNIX Perl. Perl scripts can be used in a
Windows environment, and ActivePerl directly supports use of the Windows Scripting
Host (WSH), which enables Perl scripts to be executed on WSH server systems.
258
CHAPTER 9
Integrating Active Directory in a UNIX Environment
Integration of key Microsoft technology with non-Microsoft environments is no longer an
afterthought with the maturation of the three major products detailed in this chapter. No
longer a separate product, integration with UNIX is built in to the OS with components
such as Services for NFS, the Subsystem for UNIX-based Applications, and the Identity
Management for UNIX components. Proper utilization of Windows UNIX integration
components can help to lower the total cost of ownership associated with maintaining
multiple platform environments. In addition, these technologies bring closer the lofty
ideal of bringing multiple directory environments under a single directory umbrella
through the realization of Single Sign-On, password synchronization, and other key func-
tionality that integrates directories with Windows Server 2008 R2.
The following are best practices from this chapter:
. Only install Server for NIS if the Windows server is not subservient to any UNIX
NIS servers.
ptg
. Consider using the downloadable getusers.ksh and makeusers.ksh Korn scripts to
create AD user accounts for NIS users if using SNIS is not possible in an environment.
. Use SUA to replace legacy UNIX scripts and run them in a native Windows
environment.
. Use the ForeFront Identity Manager (FIM) product for more advanced scenarios where
automatic provisioning/deprovisioning of UNIX and AD DS accounts is required.
. Use the AD DS Integration with Services for NFS, rather than the legacy User Name
Mapping service, as integration is tighter with AD DS.
IN THIS CHAPTER
Domain Name System
. Understanding the Need
for DNS
and IPv6
. Getting Started with DNS on
Windows Server 2008 R2
. Resource Records
. Understanding DNS Zones
. Performing Zone Transfers
Name resolution is a key component in any network
. Understanding DNS Queries
operating system (NOS) implementation. The capability of
any one resource to locate other resources is the centerpiece
. Other DNS Components
of a functional network. Consequently, the name-resolution
. Understanding the Evolution of
strategy chosen for a particular NOS must be robust and
Microsoft DNS
reliable, and it ideally will conform to industry standards.
. DNS in Windows Server
Windows Server 2008 R2 utilizes the domain name system
2008 R2
(DNS) as its primary method of name resolution, and DNS
ptg
. DNS in an Active Directory
is a vital component of any Active Directory implementa-
Domain Services Environment
tion. Windows Server 2008 R2’s DNS implementation was
designed to be compliant with the key Request for
. Troubleshooting DNS
Comments (RFCs) that define the nature of how DNS
. IPv6 Introduction
should function. This makes it particularly beneficial for
existing network implementations, as it allows Windows
. How to Configure IPv6 on
Windows Server 2008 R2
Server 2008 R2 to interoperate with other types of RFC-
