Windows Server 2008 R2 Unleashed (135 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

account audit policies, trust policies) is made, the event is recorded.
.
Audit privilege use—
Privileged use is a security setting and can include a user
employing a user right, changing the system time, and more. Successful or unsuc-
cessful attempts can be logged.
.
Audit process tracking—
An event can be logged for each program or process that
a user launches while accessing a system. This information can be very detailed and
take a significant amount of resources.
.
Audit system events—
The system events policy logs specific system events such as
ptg
a computer restart or shutdown.
The audit policies can be enabled or disabled through the local system policy, domain
controller security policy, or Group Policy Objects. Audit policies are located within the
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit
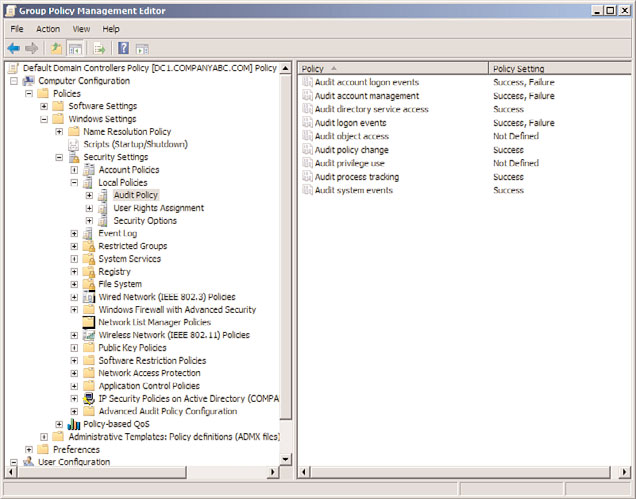
Policy folder of the Group Policy Management Editor, as shown in Figure 20.12.
For the audit policies, the recommended settings are given in Table 20.3. These should be
set on the Default Domain and Default Domain Controller GPOs. By default, all the poli-
cies are Not Defined. Figure 20.12 shows the recommended settings.
TABLE 20.3
Matching Audit Policies Recommended Settings
Audit Policy
Recommended Setting
Audit account logon events
Success and Failure
Audit account management
Success and Failure
Audit directory service access
Success
Audit logon events
Success and Failure
Audit object access
Not Defined
Audit policy change
Success
Audit privilege use
Not Defined
Audit process tracking
Success
Audit system events
Success
Auditing the Environment
667
ptg
FIGURE 20.12
Audit policies and the recommended settings.
The recommended settings are designed to address specific threats. These threats are
primarily password attacks and misuse of privilege. Table 20.4 matches the threats to the
specific audit policies.
TABLE 20.4
Matching Specific Threats to Audit Policy Recommended Settings
Threat Addressed
Audit Policy
Random password attacks
Audit account logon events (failures)
Audit logon events (failures)
Stolen password attacks
Audit account logon events (successes)
Audit logon events (successes)
Misuse of privileges
Audit account management
20
Audit directory service access
Audit policy change
Audit process tracking
Audit system events
668
CHAPTER 20
Windows Server 2008 R2 Management and Maintenance Practices
These recommended settings are sufficient for the majority of organizations. However,
they can generate a heavy volume of events in a large organization. Or, there might be a
subset of security events that an organization needs to track. In those cases, the next
section discusses how to fine-tune the audit policy using audit policy subcategories.
Audit Policy Subcategories
Windows Server 2008 R2 allows more granularity in the setting of the audit policies. In
previous versions of the Windows Server platform, the audit policies could only be set on
the general categories. This usually resulted in a large number of security events, many of
which are not of interest to the administrator. System management software was usually
needed to help parse all the security events to find and report on the relevant entries.
Windows Server 2008 R2 exposes additional subcategories under each of the general cate-
gories, which can each be set to No Auditing, Success, Failure, or Success and Failure.
These subcategories allow administrators to fine-tune the audited events.
Unfortunately, the audit categories do not quite match the audit policies. Table 20.5
shows how the categories match the policies.
TABLE 20.5
Matching Audit Policies to Audit Categories
ptg
Audit Policy
Audit Category
Audit account logon events
Account Logon
Audit account management
Account Management
Audit directory service access
DS Access
Audit logon events
Logon/Logoff
Audit object access
Object Access
Audit policy change
Policy Change
Audit privilege use
Privilege Use
Audit process tracking
Detailed Tracking
Audit system events
System
There are over 50 different subcategories that can be individually set. These give the admin-
istrator and security professionals unprecedented control over the events that will generate
security log entries. Table 20.6 lists the categories and the subcategories of audit policies.
Auditing the Environment
669
TABLE 20.6
Audit Subcategories
Audit Category
Audit Subcategory
System
Security State Change
Security System Extension
System Integrity
IPSec Driver
Other System Events
Logon/Logoff
Logon
Logoff
Account Lockout
IPSec Main Mode
IPSec Quick Mode
IPSec Extended Mode
Special Logon
Network Policy Server
Other Logon/Logoff Events
Object Access
File System
ptg
Registry
Kernel Object
SAM
Certification Services
Application Generated
Handle Manipulation
File Share
Filtering Platform Packet Drop
Detailed File Share
Filtering Platform Connection
Other Object Access Events
Privilege Use
Sensitive Privilege Use
Non-Sensitive Privilege Use
Other Privilege Use Events
Detailed Tracking
Process Creation
Process Termination
20
DPAPI Activity
RPC Events
670
CHAPTER 20
Windows Server 2008 R2 Management and Maintenance Practices
TABLE 20.6
Audit Subcategories
Audit Category
Audit Subcategory
Policy Change
Audit Policy Change
Authentication Policy Change
Authorization Policy Change
MPSSVC Rule-Level Policy Change
Filtering Platform Policy Change
Other Policy Change Events
Account Management
User Account Management
Computer Account Management
Security Group Management
Distribution Group Management
Application Group Management
Other Account Management Event
DS Access
Directory Service Access
Directory Service Changes
Directory Service Replication
ptg
Detailed Directory Service Replication
Account Logon
Kerberos Service Ticket Operations
Credential Validation
Kerberos Authentication Service
Other Account Logon Events
You can use the AUDITPOL command to get and set the audit categories and subcate-
gories. To retrieve a list of all the settings for the audit categories and subcategories, use
the following command:
auditpol /get /category:*
To enable auditing of the Distribution Group Management subcategory of the Account
Management category for both success and failure events, the following command can be
used:
auditpol /set /subcategory:”Distribution Group Management”
/success:enable /failure:enable
This command would need to be run on each domain controller for the policy to have a
uniform effect. To get all the options for the Audit Policy command, use the following
command:
auditpol /?
Auditing the Environment
671
Auditing Resource Access
Object access can be audited, although it is not one of the recommended settings.
Auditing object access can place a significant load on the servers, so it should only be
enabled when it is specifically needed. Auditing object access is a two-step process: Step
one is enabling “Audit object access” and step two is selecting the objects to be audited.
When enabling Audit object access, you need to decide if both failure and success events
will be logged. The two options are as follows:
. Audit object access failure enables you to see if users are attempting to access objects
to which they have no rights. This shows unauthorized attempts.
. Audit object access success enables you to see usage patterns. This shows misuse of
privilege.
Enable the appropriate policy setting in the Group Policy Object. It is a best practice to
apply the GPO as close to the monitored system as possible, so avoid enabling the audit-
ing on too wide a set of systems.
NOTE
Monitoring both success and failure resource access can place additional strain on the
ptg
system. Success events can generate a large volume of events.
After enabling the object access policy, the administrator can make auditing changes
through the property pages of a file, folder, or a Registry key. If the object access policy is
enabled for both success and failure, the administrator will be able to audit both successes
and failures for a file, folder, or Registry key.
After object access auditing is enabled, you can easily monitor access to resources such as
folders, files, and printers.
Auditing Files and Folders
The network administrator can tailor the way Windows Server 2008 R2 audits files and
folders through the property pages for those files or folders. Keep in mind that the more
files and folders that are audited, the more events that can be generated, which can
increase administrative overhead and system resource requirements. Therefore, choose
wisely which files and folders to audit. To audit a file or folder, do the following:
1. In Windows Explorer, right-click the file or folder to audit and select Properties.
20
2. Select the Security tab and then click the Advanced button.
3. In the Advanced Security Settings window, select the Auditing tab and click the
Edit button.
4. Click the Add button to display the Select User or Group window.
5. Enter the name of the user or group to audit when accessing the file or folder. Click
the Check Names button to verify the name.
672
CHAPTER 20
Windows Server 2008 R2 Management and Maintenance Practices
6. Click OK to open the Auditing Entries window.
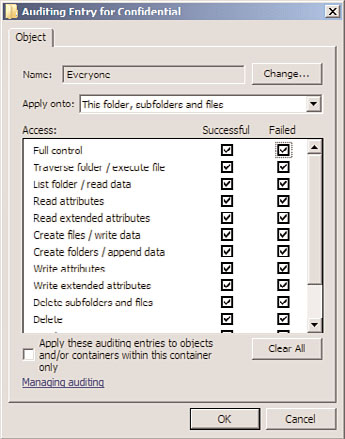
7. In the Auditing Entry window, shown in Figure 20.13, select which events to audit
for successes or failures.
ptg
FIGURE 20.13
The Auditing Entry window.
8. Click OK four times to exit.
NOTE
This step assumes that the audit object access policy has been enabled.
When the file or folder is accessed, an event is written to Event Viewer’s security log. The
category for the event is Object Access. An Object Access event is shown in the following
security log message:
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Date: 9/28/2009 6:22:56 PM
Event ID: 4663
Task Category: File System
Level: Information
Keywords: Audit Success
User: N/A
Computer: DC1.companyabc.com
Auditing the Environment
673
Description:
