Windows Server 2008 R2 Unleashed (126 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

related to that particular policy.
Separation of GPO Functions
Determining which features and settings of a GPO will be utilized is one consideration;
another is determining how to deploy those settings. There is one major consideration
19
with GPO management that should be considered: Should a single GPO be created to
contain all the necessary settings, or should separate GPOs be created for a particular set
of features or functions?
As a best practice, separating GPO functions across multiple GPOs provides more flexibil-
ity but also adds time to GPO processing and increases the amount of GPO administration
that needs to be performed. Separating GPOs for specific functions provides additional
troubleshooting options and greater flexibility for how GPOs can be linked and filtered. As
an example of how to separate GPO functions, the following list of GPOs can be applied
to a Branch Office OU that contains user objects, group objects, and computer objects:
.
Branch Office Help Desk GPO—
This GPO would configure settings to allow help
desk administrators to manually run Windows Update, access all Control Panel
618
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
applets, and run all software with unrestricted access. This would be the last GPO
applied and would override any conflicting settings. This GPO status would be set to
Computer Configuration Settings Disabled and the security filtering would be
configured to use a security group called Branch Office Help Desk, which would
include the help desk support staff.
.
Branch Office Server GPO—
This GPO can contain the default security settings
and software packages specific for branch office servers. Also this policy would
configure specific audit settings, account management settings, and user rights
assignments for servers. The GPO status would be configured for User Configuration
Settings Disabled and would have a WMI filter linked that includes computers with
an operating system name that includes the word server.
.
Branch Office User GPO—
This GPO can contain the default security and configu-
ration settings to configure the end-user desktop environment, including managing
Microsoft Internet Explorer settings, redirecting folders to the branch office DFSR
shares, enabling offline files, mapping network drives, installing network printers,
and configuring settings to hide or restrict access to specific Control Panel applets.
The GPO status of this GPO would be configured to Computer Configuration
Settings Disabled.
.
Branch Office Workstation GPO—
This GPO can contain the default security set-
ptg
tings used to manage the services, install corporate software packages and VPN
clients, configure workstation security, and enable remote access. This GPO would be
filtered using a WMI filter that includes only computer objects whose operating sys-
tem name value contained Windows 7. The GPO status would be set to User
Configuration Settings Disabled. This GPO would be applied first to the workstations
after local and inherited GPOs.
Separation of GPO by Targeted Operating System
With each release of a Microsoft client or server operating system, Microsoft provides new
Group Policy settings and functionality. The release of Windows 7 and Windows Server
2008 R2 is no different as there are several new Group Policy settings that will not apply
to any other operating systems. These include both policy and preference settings to
manage. Some of the preferences include managing power settings on Windows Vista and
newer operating systems as well as adding scheduled tasks and immediately scheduled
tasks that will run at the next Group Policy refresh cycle. These preferences are detailed in
Chapter 27.
When operating system–specific Group Policy settings will be used, a best practice is to
filter out all other operating systems the GPO applies to. The best way to do this is with
the use of a WMI filter for computers. Security filtering can also be used but if a security
group is used, a computer will only pick up group changes during startup, so getting
application of a new policy adopted is less successful. A WMI filter will be processed by all
GPO Administrative Tasks
619
Windows XP, Windows Vista, Windows 7, Windows Server 2003, or Windows Server 2008
systems. How to create a WMI filter is detailed later in this chapter in the section
“Creating and Linking WMI Filters to GPOs.”
This section of the chapter includes detailed steps an administrator can perform to execute
GPO-related administrative tasks.
Installing the Group Policy Management Tools
Before Group Policy can be managed, the Group Policy Management Tools must be
installed. These tools are installed by default on Windows Server 2008 R2 domain
controllers, but for other systems, they must be manually installed. The following sections
detail installation steps for Windows Server 2008 R2 and Windows 7 systems.
Installing the Group Policy Management Tools on Windows Server 2008 R2
ptg
Before group policies can be managed from a Windows Server 2008 R2 system, the Group
Policy Management feature must be installed, as detailed in the following steps:
1. Log on to a designated administrative system running Windows Server 2008 R2.
2. Open Server Manager from the Administrative Tools menu.
3. After Server Manager loads, click on the Features node in the tree pane.
4. Select Add Features in the right pane.
5. Scroll down and check the box next to Group Policy Management and click Next.
6. Confirm the selection and click Install to begin the process.
7. After the process completes, click Close to complete the installation.
Installing the Group Policy Management Tools on Windows 7
To manage domain group policies from a Windows 7 system, the administrator must
19
download the “Remote Server Administration Tools for Windows 7” from the Microsoft
download site. After the tool is downloaded, it must be installed on the Windows 7
system by an administrator. Once the tool is installed, the Group Policy Management
feature can be installed from Control Panel, as detailed in the following steps:
1. Log on to a designated administrative system running Windows 7 after the Remote
Server Administration Tools for Windows 7 are installed.
2. Open Control Panel from the Start menu.
620
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
3. Select Programs and click on the Turn Windows Features On or Off link.
4. Scroll down and expand Remote Server Administration Tools.
5. Expand Feature Administration Tools and check the box next to Group Policy
Management Tools.
6. Click OK on the Windows Features window to begin the installation.
7. Once the installation completes, close Control Panel.
After these steps are completed, the Group Policy Management feature can be accessed
from the Administrative Tools menu. Installing these tools also installs the Group Policy
module for PowerShell.
Managing Group Policy with Windows PowerShell
From a Windows 7 or a Windows Server 2008 R2 system with the Group Policy
Management Tools installed, several new Windows PowerShell cmdlets can be leveraged to
manage Group Policy. To access these Group Policy cmdlets, follow these steps:
1. Log on to a designated administrative system running Windows 7 or Windows
Server 2008 R2.
2. Click the Start or Windows button on the taskbar and in the search pane type in
ptg
PowerShell.
3. When the results are shown, right-click Windows PowerShell and select Run as
Administrator.
4. In the PowerShell window, type Import-module grouppolicy and press Enter to
enable Group Policy management.
5. Now in the window, type Get-command *GP* -commandtype cmdlet and press Enter
to see a list of the 25 different Group Policy cmdlets available.
6. To get help information on a specific Group Policy cmdlet, such as “get-gporeport”,
type Get-help get-gporeport and press Enter.
7. And to see syntax usage of a specific cmdlet such as “get-gporeport”, type Get-help
get-gporeport –example and press Enter to see several different examples.
Creating a GPO Central Store
Starting with Windows Vista and Windows Server 2008, administrators now have the
ability to manually create a folder on the Active Directory domain controller that
contains all of the necessary ADMX and ADML files. This folder is referred to as the GPO
central store and will need to be created and managed manually. The GPO central store
can be created in a domain that contains at least Windows Server 2003 domain
controllers or greater.
By default, with Windows Vista, Windows 7, Windows Server 2008, and Windows Server
2008 R2, when a GPO is opened for editing on one of these operating systems, the system
first checks the domain controller to which the GPO management tool is connected for
the existence of a GPO central store. If the folder exists, the GPO loads the templates
GPO Administrative Tasks
621
stored in the folder. If the central store does not exist, the local copies of the ADMX and
ADML files are loaded to view the GPO.
NOTE
For a central store to work properly, the Active Directory Forest and Domain Schema
must be upgraded to at least Windows Server 2008 Schema.
The creation of the GPO central store provides a simple, yet effective way for administra-
tors to manage administrative templates from the server. To create the GPO central store,
perform the following steps:
1. Log on to a designated administrative system running Windows Vista, Windows 7,
Windows Server 2008, or Windows Server 2008 R2.
2. Browse to the C:\Windows\ folder and copy the PolicyDefinitions folder to the
Clipboard.
3. In a domain named companyabc.com, open the following folder:
\\companyabc.com\sysvol\companyabc.com\policies.
ptg
4. Paste the PolicyDefinitions folder from the Clipboard to the folder referenced in the
preceding step.
5. Close any open folder windows.
The preceding steps create the central store and populate the store with the ADML
language files of the administrative workstation. If additional language files are required,
the language subfolder within the PolicyDefinitions folder of the administrative worksta-
tion can be copied into the domain’s central store now located at
\\companyabc.com\sysvol\companyabc.com\policies\PolicyDefinitions.
Verifying the Usage of the GPO Central Store
To verify whether the central store is actually being used, perform the following steps:
1.
19
Log on to a designated administrative system.
2. Open the Group Policy Management Console.
3. Expand the domain to expose the Group Policy Objects container and expand it.
4. Select any existing GPO that contains at least one configured setting within the
Administrative Templates section of either the Computer Configuration or User
Configuration node.
5. In the right pane, select the Settings tab to view the settings of the GPO, similar to
the settings shown in Figure 19.18.
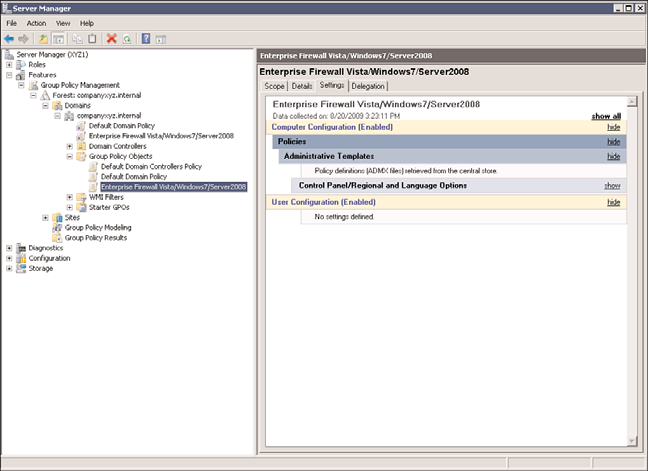
622
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
ptg
FIGURE 19.18
Examining Group Policy settings.
6. Under Administrative Templates, it will state whether policy definitions (ADMX)
files were retrieved from the local machine or from the central store.
7. Close the Group Policy Management Console.
Creating and Utilizing Starter GPOs
The Windows 7 and Windows Server 2008 R2 GPMC includes a feature and GPO function
named starter GPOs. This function allows administrators to create or load base GPOs with
preconfigured administrative template settings and values, which can be used to prepopu-
late new GPOs. If any starter GPOs exist, an administrator creating a new GPO from a
Windows 7 or a Windows Server 2008 R2 GPMC console will have the option of using any
existing starter GPO to prepopulate newly created GPOs with a number of setting values.
Once the starter GPO functionality is enabled, Group Policy administrators can create new
