Windows Server 2008 R2 Unleashed (120 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

sections contain the Group Policy settings that will determine how often a policy will be
refreshed, if a policy will be reapplied even if the revision number has not changed since
the last cycle, and if the policy will be applied across slow links or if any local computer
policies will be processed by a computer or a user.
ptg
FIGURE 19.1
Examining Group Policy settings.
Two different types of policies can be applied to Windows systems and Windows system
user accounts: local group policies and Active Directory group policies. Local group poli-
cies exist on all Windows systems, but Active Directory group policies are only available in
an Active Directory forest. Until the release of Windows Vista and Windows Server 2008,
servers and workstations could contain and apply only a single local computer and user
policy. This policy contained the settings that could be applied to the local computer and
the user objects to control the security and configuration settings.
In many environments, usually due to legacy or line-of-business application requirements,
end users were frequently granted local Administrators group membership on worksta-
tions and essentially excluded from the application of many security settings applied by
both the local and group policies. End users with local Administrators group membership
Local Group Policies
589
have the ability to override settings and make configuration changes that could compro-
mise the security, or more frequently, reduce the reliability of the system.
Starting with Windows Vista and Windows Server 2008, administrators now have the
ability to create multiple local group policies. One of the new features is that specific user
group policies can be created for all users, for users who are not administrators, and for
users who are members of the local Administrators group on the computers. This new
feature can be especially valuable for computers configured in workgroup or standalone
configurations to increase the security and reliability of the computer. In domain configu-
rations, computer security policies are usually specified using group policies and applied to
the Active Directory computers.
Local Computer Policy
The default local computer policy contains out-of-the-box policy settings, as shown in
Figure 19.2, which are available to configure the computer and user environment. This
policy will be applied first for both computer and user objects logging on to the worksta-
tion in workgroups or domains.
ptg
19
FIGURE 19.2
Examining local computer policy settings.
Local User Policies for Non-Administrators and Administrators
Starting with Windows Vista and Windows Server 2008, and continuing with Windows 7
and Windows Server 2008 R2, administrators now have the option to create multiple local
user group policies on a single machine. In previous versions, the single local computer
policy allowed administrators to apply the single policy settings to all users logging on to
590
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
a workstation that is part of a workgroup. Now, workgroup computers and domain
computers can have additional policies applied to specific local users. Also, policies can be
applied to local computer administrators or nonadministrators. This allows the worksta-
tion administrator to leave the user section of the default local computer policy blank,
and create a more-restrictive policy for local users and a less-restrictive policy for members
of the local workstation Administrators security group.
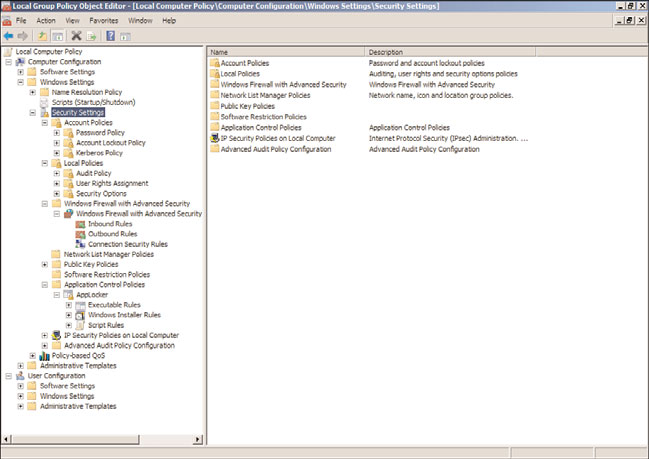
Within each local computer policy and within a GPO Computer Configuration node,
there is a section named Security Settings, as shown in Figure 19.3. This section includes
settings for computer audit policies, account management settings, and user rights assign-
ments. This section of the policy is unique because it can be imported and exported indi-
vidually. In previous versions of Windows, several security templates were provided out of
the box to give administrators the ability to quickly load a set of best-practice security
configuration settings. These templates included basic workstation and server templates
along with high security, compatible security, and domain controller security templates.
ptg
FIGURE 19.3
Examining the computer security section.
To manage and apply a standard set of security configurations to workgroup or standalone
systems, administrators can leverage the management functions of security templates.
Either using the Group Policy Object Editor, the Local Security Policy editor, or the
Security Configuration and Analysis MMC snap-in, administrators can import a base
template, configure or adjust settings to meet the desired security settings, and export and
Elements of Group Policy
591
save the settings to a custom template file. This custom template file could then be
imported or applied to all the desired systems using the tools referenced previously.
Security templates exist for Windows Vista, Windows 7, Windows Server 2008, and
Windows Server 2008 R2. These base security templates are located in the
%systemroot%\inf folder or on a default install, c:\windows\inf. The default security
templates all start with the name deflt and end with an .inf extension. For example, on
Windows Server 2008 R2, the templates that exist are named defltbase.inf, defltsv.inf,
and defltdc.inf. These files can be used to configure a system’s security settings to a
standard set of security configurations.
CAUTION
Importing security templates to servers or workstations already deployed can cause
several issues, including losing the ability to log on or access the system from the net-
work. Please make sure to test any changes to security settings when working with the
import and application of security templates.
ptg
This section of the chapter provides an overview of the concepts and terminology of the
elements of Group Policy to provide system administrators with the information required
to understand, support, and deploy group policies in an Active Directory forest. As a
follow-up to this chapter, Chapter 27, “Group Policy Management for Network Clients,”
provides useful best-practice examples of how Group Policy can be deployed to simplify
the management and configuration of your Active Directory servers, workstations, and
users. Although some administrators might be inclined to skip the remainder of this
chapter and jump right to Chapter 27, it is highly recommended that you review this
chapter to understand how to manage the Group Policy infrastructure before attempting
to manage the devices in the Active Directory forest.
Group Policy Objects
The elements of Group Policy start with the Group Policy Objects (GPOs) themselves.
19
GPOs are a predefined set of available settings that can be applied to Active Directory
computer and/or user objects. The settings available within a particular GPO are created
using a combination of administrative template files included or referenced within that
GPO. As the particular computer or user management needs change, additional adminis-
trative templates can be imported into a particular GPO to extend its functionality.
Group Policy Object Storage and Replication
GPOs are stored in both the file system and the Active Directory database. Each domain in
an Active Directory forest stores a complete copy of that particular domain’s GPOs.
Within Active Directory, the GPO links and version information are stored within the
domain naming context partition of the database. Because this partition is only replicated
592
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
within a single domain, processing GPOs linked across domains, either using sites or just a
cross-domain GPO link, can take longer to load and process.
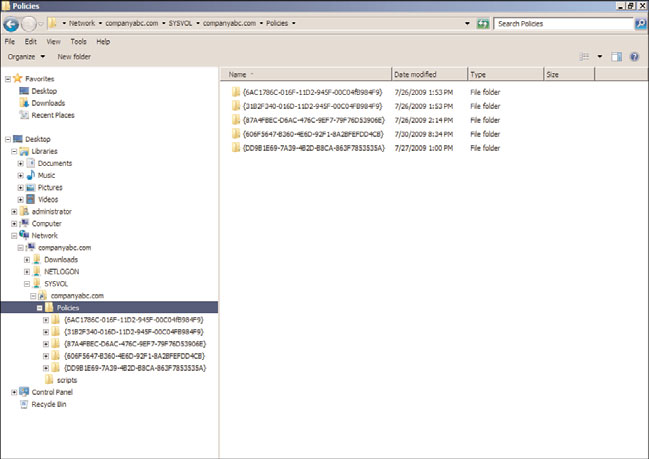
The GPO settings are stored in the file system of all domain controllers within the sysvol
folder. The sysvol folder is shared on all domain controllers. Each domain GPO has a
corresponding folder located within the sysvol\companyabc.com\Policies subfolder, as
shown in Figure 19.4 as an example of the companyabc.com domain. The GPO folder is
named after the globally unique identifier (GUID) assigned to that GPO during creation.
The GUID of a GPO is listed when viewing the properties of a domain GPO using the
Group Policy Management Console. Within the GPO folder are a common set of subfold-
ers and files, including the User folder, Machine folder, sometimes the ADM folder, and
the gpt.ini file.
ptg
FIGURE 19.4
Examining the sysvol Policies folder.
Group Policy Object Replication
Because GPOs are stored within the Active Directory database and on the domain controller
file system, all GPO information is replicated by the domain controllers. The file system
portion of the domain GPOs is replicated within the Domain System Volume Distributed
File System Replication group by the Distributed File System Replication service.
The Domain System Volume replication schedule is controlled by the DFSR schedule,
which, by default, follows the same replication cycle as the Active Directory database.
Replication occurs every 5 minutes or immediately between domain controllers in a single
Active Directory site and follows the site link schedule between domain controllers in
separate sites. Legacy domains will use the File Replication Service instead of DFSR.
Elements of Group Policy
593
User Subfolder
The User subfolder contains the files and folders used to store the settings, software,
scripts, and any other policy settings specific to user and user object policies configured
within a particular GPO.
Machine Subfolder
The Machine subfolder contains the files and folders used to store the settings, software,
scripts, and any other policy settings specific to machine or computer object policies
configured within a particular GPO.
ADM Subfolder
The ADM subfolder is created on new GPOs when legacy administrative template files are
imported into a GPO. Any GPOs created using Windows 2000 and Windows XP client
software, or Windows 2000 Server and Windows Server 2003 system software, will contain
