Windows Server 2008 R2 Unleashed (214 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

Managing Active Directory with Policies
1091
7. When the Group Policy Management Editor opens, expand Computer
Configuration, expand Policies, and select the Administrative Templates node.
8. Beneath the Administrative Templates node, expand System, and select Logon in
the tree pane.
9. In the Settings pane, double-click on the Always Wait for the Network at Computer
Startup and Logon setting.
10. On the setting tab, select the Enabled option button, and click OK, as shown in
Figure 27.32.
ptg
27
FIGURE 27.32
Enabling Synchronous Foreground Group Policy processing.
11. Close the Group Policy Management Editor, and return to the GPMC.
12. In the GPMC, if necessary, adjust the links to the updated GPO and close the GPMC
when finished.
GPO Modeling and GPO Results in the GPMC
When an organization decides to perform administrative and management tasks using
group policies, it is essential that the system administrators understand how to check to
see if Group Policy processing is working correctly. In the case when Active Directory hier-
archies are being restructured, or if new policies are being deployed, performing a simu-
lated application of group policies to review the results can help avoid unexpected issues.
To perform Group Policy simulations, an administrator can use Group Policy Modeling,
available in the GPMC. Group Policy Modeling is the equivalent of Resultant Set of
Policies (Planning), which is the name of the administrative right that must be delegated
1092
CHAPTER 27
Group Policy Management for Network Clients
in Active Directory to run this tool. To perform Group Policy Modeling, perform the
following tasks:
1. Log on to a designated Windows Server 2008 R2 administrative server.
2. Open the Group Policy Management Console from the Administrative Tools menu.
3. In the tree pane, select the Group Policy Modeling node, right-click the node, and
select Group Policy Modeling Wizard.
4. On the Welcome page, click Next to continue.
5. On the Domain Controller Selection page, specify a domain controller or accept the
default of using any domain controller, and click Next.
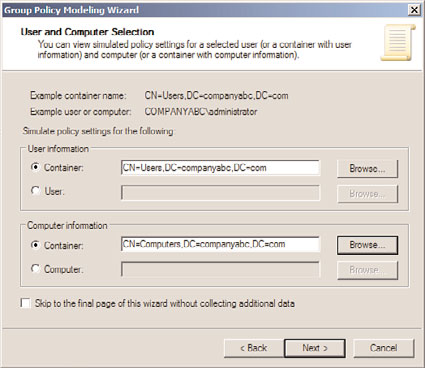
6. On the User and Computer Selection page, the Group Policy Modeling Wizard can
be used to run a simulation based on a specific user and computer in their current
locations, or containers can be specified for either the user or computer to simulate
GPO processing of a specific user, logging on to a Computer in a specific container.
For this example, select the Users container and the Computers container of the
domain to determine which policies and settings will be applied by default, as
shown in Figure 27.33. Click Next to continue.
ptg
FIGURE 27.33
Selecting the default user and computer containers for Group Policy Modeling.
7. On the Advanced Simulations page, loopback processing, slow network connec-
tions, and site-specific testing can be specified. Accept the defaults and click Next
to continue.
8. On the User Security Groups page, specific security groups can be specified to run
policy modeling against. Accept the defaults and click Next to continue.
9. On the Computer Security Groups page, specific security groups can be specified to
run policy modeling against. Accept the defaults and click Next to continue.
Managing Active Directory with Policies
1093
10. On the WMI Filters for Users page, select the All Linked Filters option button, and
click Next to continue.
11. On the WMI Filters for Computers page, select the All Linked Filters option button,
and click Next to continue.
12. On the Summary of Selections page, review the choices and if everything looks
correct, click Next to run the GPO modeling tool.
13. When the process completes, click Finish to return to the GPMC and review the
modeling results.
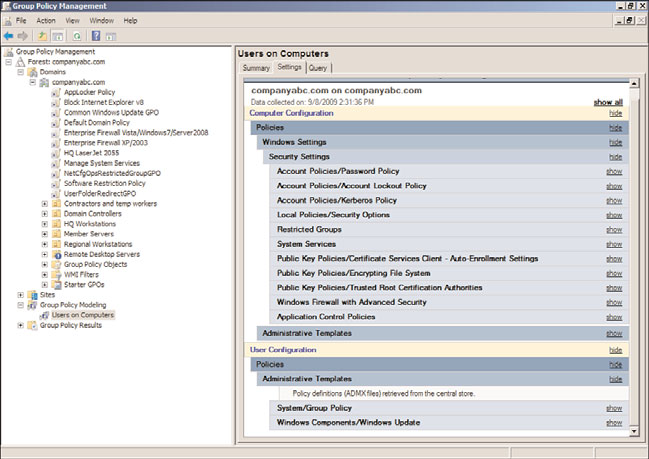
14. In the Settings pane, the summary of the computer and user policy processing will
be available for view. Review the information on this page and then click on the
Settings tab to review the final GPO settings that would be applied, as shown in
Figure 27.34.
ptg
27
FIGURE 27.34
Reviewing the GPO modeling resultant settings.
15. Close the GPMC and log off.
In situations when Group Policy is not delivering the desired results, GPO Results can be
run to read and display the Group Policy processing history. GPO Results are run against a
specific computer, but can also be used to collect user policy processing. To run GPO
Results to review the GPO processing history, perform the following steps:
1. Log on to a designated Windows Server 2008 R2 administrative server.
2. Open the Group Policy Management Console from the Administrative Tools menu.
3. In the tree pane, select the Group Policy Results node, right-click the node, and
select Group Policy Results Wizard.
1094
CHAPTER 27
Group Policy Management for Network Clients
4. On the Welcome page, click Next to continue.
5. On the Computer Selection page, choose to run the policy against another computer
and locate a Windows 7 system that a user has already logged on to. Also be sure to
uncheck the Do Not Display Policy Settings for the Selected Computer in the Results
check box, and click Next.
6. On the User Selection page, select the Display Policy Settings For option button, and
then select the Select a Specific User option button. Select a user from the list, and
click Next to continue. Only users who have previously logged on to the selected
computer will be listed and they will only be listed if the user running the tool is a
domain admin or has been granted the right to run Resultant Set of Policies
(Logging) for the particular users.
7. On the Summary of Selections page, review the choices and click Next to start the
GPO Results collection process.
8. When the process completes, click Finish to return to the GPMC.
9. When the process completes, the results will be displayed in the Settings pane on
the Summary, Settings, and Policy Events tabs. Review the results and close the
GPMC when finished.
Managing Group Policy from Administrative or Remote Workstations
ptg
It is very common for Windows system administrators to manage group policies from
their own administrative workstations. To manage a Windows Server 2008 R2 environ-
ment properly, domain group policy administration should be performed using a
Windows Server 2008 R2 or Windows 7 system with the Group Policy Management tools
and the Print Services tools installed. The main reason for this is that by using the latest
version of the tools possible, the administrator ensures that all possible features are avail-
able and that the most stable version of the tools are being used.
Group Policy management, aside from creating and managing policies, provides adminis-
trators with the ability to simulate policy processing for users and computers in specific
containers in Active Directory using the Group Policy Modeling node in the GPMC.
Furthermore, the previous application of Group Policy for users and computers can be
collected and reviewed in the Group Policy Management Console using the Group Policy
Results node in the GPMC. For an administrator, even a member of the Domain Admins
group, to perform remote Group Policy Modeling using the GPMC from a machine other
than a domain controller, the following requirements must be met:
. The administrator must be a member of the domain Distributed COM Users secu-
rity group.
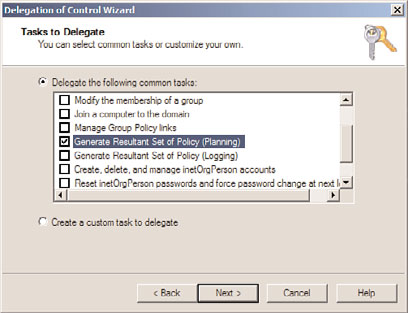
. The administrator must be delegated the Generate Resultant Set of Policy (Planning)
right in Active Directory, as shown in Figure 27.35. This right must be applied to the
domain, OU, container, or site that contains all of the computers and users the
administrator will run simulated GPO processing against.
. The administrator must have the right to read all the necessary group policies, and
this should be allowed by default.
Summary
1095
FIGURE 27.35
Delegating the Generate Resultant Set of Policy (Planning) right.
To perform remote Group Policy Results tasks using the GPMC from a machine other than
a domain controller, the following requirements must be met:
. The administrator must be a member of the remote computer’s local Distributed
COM Users security group.
ptg
. The administrator must be a member of the remote computer’s local Administrators
security group for legacy desktop platforms and the remote system must be accessi-
ble on the network.
. The Windows Firewall must be configured to allow the inbound Remote
27
Administration exception and the remote workstation must be on a network that is
defined within this exception.
. The administrator must be delegated the Generate Resultant Set of Policy (Logging)
right in Active Directory. This right must be applied to the domain, OU, container,
or site that contains all of the computers and users the administrator will run simu-
lated GPO processing against.
. The administrator must have the right to read all the necessary group policies, and
this should be allowed by default.
Windows Server 2008 R2 Group Policy provides administrators with many options to stan-
dardize configuration and management of users and computer settings. Management poli-
cies can be fine tuned based on the function, location, and security needs of the users or
the security requirements of the organization. This chapter offers many suggestions and
examples of how Group Policy can be leveraged in any organization. Although group poli-
cies are very functional and can be a very attractive option for user and computer manage-
ment, the planning and testing of group policies is essential in delivering the desired
1096
CHAPTER 27
Group Policy Management for Network Clients
configuration and security settings to users and computers in an Active Directory or
Windows workgroup environment.
The following are best practices from this chapter:
. The only changes that should be made to the default domain policy should be
modifying the password and account policy settings and nothing else.
. When the local or domain Administrator user account is a member of a group that
will be managed with domain group policy restricted groups, do not count on the
