Windows Server 2008 R2 Unleashed (208 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

Server 2008 R2 contain three firewall profiles, including the domain profile, the private
profile, and the public profile. The domain profile remains the same, but the previous
standard profile has now been segmented into the private and public profiles. Any
network that is different from the domain network is initially categorized as an untrusted
network and the public firewall profile is activated. End users, with the appropriate rights,
can define a public network as a private network, which can then activate the private fire-
wall profile and the appropriate firewall rule set, which is likely to be less restrictive and
might allow the necessary traffic for the remote client to work correctly on the network
they are connected to. Windows Firewall design and configuration planning is a very
important task for Windows administrators to execute and should not be taken lightly.
Also, disabling firewalls in any profile is not recommended and is a poor approach to
enabling systems and applications to function on an organization’s network.
To allow Windows administrators to continue to manage and administer Windows server
and desktop systems remotely, certain firewall exceptions should be defined. Aside from
enabling Remote Desktop, as outlined in the previous section, remote administrators
might need to copy files to and from systems and utilize Microsoft Management Console
snap-ins such as Windows Server Backup, Event Viewer, Computer Management, and
many others from remote administrative workstations. To enable the Remote Desktop and
Remote Administration exceptions in the Windows Firewall using domain group policies,
perform the following steps:
Managing Computers with Domain Policies
1063
1. Log on to a designated Windows Server 2008 R2 administrative server.
2. If necessary, install the Group Policy Management Console on the system, as
detailed previously in this chapter.
3. After the tools are installed, click Start, click All Programs, click Administrative Tools,
and select Group Policy Management.
4. Add the necessary domains to the GPMC as required.
5. Expand the Domains node to reveal the Group Policy Objects container.
6. Either create a new GPO or edit an existing GPO.
7. After the GPO is opened for editing in the Group Policy Management Editor, expand
the Computer Configuration node, expand the Policies node, and select the
Administrative Templates.
8. Expand the Administrative Templates node, expand the Network node, expand the
Network Connections node, and select the Windows Firewall node. Configurations
made in this section apply to Windows XP, Windows Vista, Windows 7, Windows
Server 2003, Windows Server 2008, and Windows Server 2008 R2. However, for more
granular firewall configuration for Windows Vista and later operating systems, the
Windows Firewall with Advanced Security setting can be used.
9. In the tree pane, expand the Windows Firewall node to reveal the Domain Profile
ptg
node, and select it.
10. In the Settings pane, locate the setting named Windows Firewall: Allow Inbound
Remote Administration Exception, and double-click on it to open the setting for
editing.
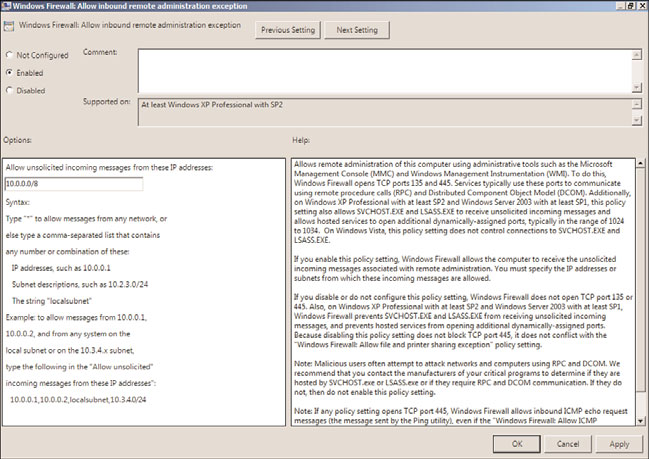
11. In the Setting window, click the Enabled option button, and type in the network
27
from which inbound remote administration will be allowed. For this example,
consider an organization that utilizes the 10.0.0.0 network with a subnet mask of
255.0.0.0. This would be defined as 10.0.0.0/8 in the properties of this exception, as
shown in Figure 27.16. When finished, click OK to update the setting.
12. After the previous setting has been configured, back in the Settings pane, select the
Windows Firewall: Allow Inbound Remote Desktop Exceptions, and double-click on
it to open the setting for editing.
13. In the setting window, click the Enabled option button, and type in the network
from which inbound Remote Desktop connections will be allowed. When finished,
click OK to update the setting.
14. If necessary, repeat the process of configuring the inbound remote administration
and Remote Desktop exception in the standard profile to ensure that remote
management from the defined network will function regardless of which firewall
profile is currently activated on the client.
1064
CHAPTER 27
Group Policy Management for Network Clients
FIGURE 27.16
Enabling the Windows Firewall remote administration exception from the
ptg
10.0.0.0/8 network.
NOTE
If the network defined within a Windows Firewall exception is a common network, such
as 192.168.0.0/24, the configuration of these exceptions in the standard profile is
considered risky and should not be performed. Instead, work with the networking group
and VPN configurations to ensure that when users connect remotely to the network
from remote sites and through VPN connections, the system will always recognize and
apply the domain profile.
15. Back in the GPMC, link the new remote administration firewall exception GPO to an
OU with a computer that can be used to test the policy.
16. After the testing is completed, configure security filtering and possibly also WMI fil-
tering to limit the application scope of this policy and link it to the desired organiza-
tional unit(s).
Configuring Advanced Firewall Settings
Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2 have a
new and improved firewall that enables administrators to define granular inbound and
outbound firewall rules and exceptions in the default firewall profiles. Even though the
Windows Firewall is enabled and active by default on Windows Server 2008 R2, when the
Add Roles Wizard is run and a role, role service, and/or feature is added to the Windows
Server 2008 R2 system, the necessary firewall exceptions are also configured as part of the
Managing Computers with Domain Policies
1065
process. This is a major advantage compared with what was included in Windows Server
2003. However, be aware that when adding additional applications or services (that are
not included with the product) to a Windows Server 2008 system, unless the installation
of that product also has a built-in feature to enable and configure the necessary exceptions
in the firewall, the exceptions will need to be defined and configured manually. When
custom firewall rules, exceptions, and changes to the default behavior and configuration
of the firewall profiles are required, the settings need to be defined using the Windows
Firewall with Advanced Security console. If these settings need to be defined using a
domain policy, access to these policy settings are included in the Computer
Configuration\Policies\Windows Security\Security Settings\Windows Firewall with
Advanced Security settings node. One advantage of using Windows Firewall with
Advanced Security is that when a system is configured manually and all of the necessary
exceptions and rules are defined within the firewall, these rules can be exported from the
firewall and imported into a domain policy and applied from the central location to all of
the desired servers. More information on the Windows Firewall is available in Chapter 13.
Configuring Windows Update Settings
Many organizations utilize the Internet services provided by Microsoft known as Windows
Update and Microsoft Update. The main difference between the two is that Microsoft
ptg
Update also includes updates for other products such as Microsoft Office, Microsoft
Exchange Server, Microsoft SQL Server, Microsoft Internet Security and Acceleration Server,
and many more. Starting with Windows XP and Windows Server 2003, all Windows
systems are now capable of downloading and automatically installing Windows updates
out of the box. To upgrade the Windows Update client to support updates for other
Microsoft applications through Microsoft Update, these machines might need to be
27
upgraded manually, upgraded using a GPO software installation, or upgraded using
Microsoft Windows Server Update Services (WSUS). A WSUS server can be configured to
update the client software automatically, which is the preferred approach. Depending on
whether the organization utilizes an internal WSUS server or wants to utilize the
Windows/Microsoft Internet-based services to configure these settings using group poli-
cies, the settings are located in the following sections:
. Computer Configuration\Policies\Administrative Templates\Windows
Components\Windows Update
. User Configuration\Policies\Administrative Templates\Windows
Components\Windows Update
For more information and recommendations on best practices for configuring Windows
Updates, please refer to the WSUS website located at www.microsoft.com/wsus and also
located at http://technet.microsoft.com/wsus.
Creating a Wireless Policy
Wireless networks are becoming more and more common in both public and private
networks. Many organizations are choosing to deploy secure wireless networks to allow for
flexible connections and communications for mobile users, vendors, and presentation
1066
CHAPTER 27
Group Policy Management for Network Clients
rooms. As a best practice, organizations commonly deploy wireless networks as isolated
network subnets with only Internet access or the ability to connect to the company
network via VPN. As wireless networks become more sophisticated and secure, the config-
uration of a wireless network on an end user’s machine becomes complicated. In an effort
to simplify this task, wireless network configurations can be saved on USB drives and
handed off to users to install and they can also be preconfigured and deployed to
Windows systems using domain policies. Group Policy wireless policies can be created for
Windows Vista or Windows XP compatible systems as each treats and configures wireless
networks differently. Windows 7 and Windows Server 2008 systems will use the Windows
Vista wireless policies. If defined in domain policies, these wireless network settings will
only be used if no third-party wireless network management software is installed and acti-
vated on the desired systems.
Wireless networks are commonly unique to each physical location, and the GPO-config-
ured wireless policies should be applied to systems in an Active Directory site or to a
specific location-based organizational unit that contains the desired computer accounts.
Furthermore, if the wireless policy GPO contains only Windows Vista workstations for the
wireless policy, WMI filtering should be applied to the GPO so that only Windows Vista,
Windows 7, and Windows Server 2008 systems process and apply the policy. To create a
wireless network for a Windows Vista, Windows 7, and Windows Server 2008 system using
a domain policy, perform the following steps:
ptg
1. Log on to a designated Windows Server 2008 R2 administrative server.
2. Click Start, click All Programs, click Administrative Tools, and select Group Policy
Management.
3. Add the necessary domains to the GPMC as required.
4. Expand the Domains node to reveal the Group Policy Objects container.
5. Create a new GPO called WirelessPolicyGPO and open it for editing.
6. After the WirelessPolicyGPO is opened for editing in the Group Policy Management
Editor, expand the Computer Configuration node, expand the Policies node and
select Windows Settings.
7. Expand Windows Settings, expand Security Settings and select Wireless Network
(IEEE 802.11) Policies.
8. Right-click Wireless Network (IEEE 802.11) Policies and select Create a New Wireless
Network Policy for Windows Vista and Later Releases. Because this is a new group
policy, this option appears, but if the group policy already has a wireless network
policy for Windows Vista and later releases, the Windows Vista policy will be avail-
able beneath the Wireless Network policy node.
9. When the New Wireless Network Policy window opens, type in an acceptable name
and description for the policy.
10. If Windows will manage the wireless network configuration and connection of the
Windows Vista systems, check the Use Windows WLAN AutoConfig Service for
Clients check box, if it is not already checked.
