Read The Bletchley Park Codebreakers Online
Authors: Michael Smith
The Bletchley Park Codebreakers (56 page)
THE NAVAL ENIGMA
KENNGRUPPENBUCH
INDICATOR SYSTEM – USED WITH THE MAIN WARTIME CIPHERS
At the start of each cipher day (often 1200 hrs), a naval Enigma operator had to set up his machine. If it was the first day of a pair in a key-list, an officer had first to insert the rotors in the order set out in the key-list, after setting the rotor rings to the letters indicated in the list. The operator then set the external connections (
Stecker
) on his machine in accordance with the key-list.
When enciphering a signal, an operator had to let the recipient know what the message key (the rotor positions when starting to encipher a specific signal) was, without revealing its clear text to the enemy. The principal naval Enigma ciphers, such as Dolphin and Shark, therefore disguised the message key by an indicating procedure known as the
Kenngruppenbuch
(recognition group book) system. Part A of the
Kenngruppenbuch
listed all 17,576 three-letter groups (trigrams – ‘BSY’ and so on) in random order. Each standard naval Enigma signal had its own message key. There was a separate system for short signals.
To encipher a message with the system, the operator –
a) looked up an allocation list to see which columns in Part A had been assigned to his cipher (e.g. columns 251–320 or 561–620 for Shark (Triton) in July 1944), selected one of the three-letter groups in one of those columns at random for the
Schlüsselkenngruppe
(cipher indicator group, for example, for Triton), and wrote it in a special cipher form;
b) picked any column at random and chose another trigram (say VFN) as the
Verfahrenkenngruppe
(procedure indicator group, but actually the message key), and wrote it in the form under the first group;
c) inserted a letter as a null (say X), as the first letter in the
Schlüsselkenngruppe
, giving X H Y U;
d) added another null letter (say K) as the last letter of the
Verfahrenkenngruppe
, making VFNK. He then had:
XHYU
1 2 3 4
V F N K
e) encoded the vertical bigrams (XV, HF and so on) with bigram tables (which substituted pairs of letters), with XV and HF here giving BM and OG, for example. Written horizontally, these resulted in: BMOG as the first indicator group PYUD as the second indicator group. He then went to his machine, and
f) turned the rotors to the
Grundstellung
, say GRD, set out in the key-list: each naval key-list contained a series of daily
Grundstellungen
, which were employed for all signals using the cipher in question;
g) obtained the message key by typing the unencoded version of the
Verfahrenkenngruppe
(VFN) once, giving e.g. SPL;
h) set the rotors to SPL as the message key;
i) keyed the plain-text of the signal, writing down each cipher text letter as its lamp lit up (often a two-man operation).
The cipher text was transmitted in four-letter groups, preceded by BMOG PYUD. A typical message is set out in Figure AIII.l. The indicator groups were repeated at the end to reduce deciphering mistakes, making naval Enigma signals instantly recognizable to friend and foe alike.
To decipher a message, the receiving operator went through the above steps in reverse (assuming that his machine was already set to
the daily key for the cipher in question), first decoding the indicator groups, using the relevant bigram tables to obtain the enciphered message key, VFN. By typing it, he obtained SPL, to which he set his rotors. He then typed the cipher text, and wrote down the resulting letters as they lit up.
Using the
Kenngruppenbuch
system, Enigma slowed down a cipher system that was far from speedy in the first place. During a monitored discussion with a fellow prisoner, one captured U-boat radio operator was heard to comment: ‘To be frank, it takes a considerable time to encipher a WT message – even if you are right up to the mark. When I enciphered a message of 40 groups [160 letters] with the
Funkmaat
[radio petty officer], it used to take five minutes at least – and that was good going.’
The system was a strong one, except for the single daily
Grundstellung
, which made Banburismus possible, when combined with the fact that rotors I to V each had their turnover notches in different places.
Figure AIII.1 Typical naval Enigma signal, as intercepted
MMA’
1
0141/4/370
2
22
3
HNMX
4
UOLP
4
FZNM HSNS CENH VHKQ TDEB XMTR GSRK DJYP XUWQ SWED NTET MWVI AUXP XXDK TYQF QBZO DDND ULDA HNMX
4
UOLF
4
0812
5
6790
6
1. Call sign of shore transmitting station. A’ was Ä
2. Time of origin, date and serial number
3. Group count
4. Indicator groups
5. Time of intercept
6. Frequency
CILLIES
When cillies were discovered by Dilly Knox in late January 1940, they reduced enormously the work involved in using the Zygalski sheets, which was otherwise a very laborious process indeed, since up to sixty rotor orders might have to be checked. After 1 May, when the Zygalski sheets became useless, following the dropping of doubly enciphered message keys, cillies became a vital part of breaking Enigma by hand during most of 1940, even when the first usable bombe entered service in August. Although more bombes became available in 1941, cillies greatly eased the burden on them, thereby making bombes available for work against ciphers which could not otherwise have been attacked. Cillies were still valuable in 1943, and probably until a German procedural change in mid-1944.
Cillies resulted from a combination of two different mistakes in a multi-part message by some Enigma operators. The first was their practice of leaving the rotors untouched when they reached the end of the first part of a multi-part message, so that the letters then in the rotor windows, for example VEI, formed the basic setting, which was therefore transmitted in unenciphered form as usual, in the second part. Since the letter count of each message part was included in
its preamble, the starting letters (the message key) of the preceding part could be calculated within fine limits, after allowing for rotor turnovers. The second error was the inclusion of non-random message keys in the same multi-part message: the use of keyboard sequences such as ‘DFG’, ‘pronounceables’, such as ‘CIL’ itself, and guessable ends of words such as ‘LER’ (for the unenciphered message key) following ‘HIT’ (for the Grund). The second type of error corroborated the first. It was vital: without it, the cryptanalysts would have been searching for will-o’-the-wisps.
The Hut 6 cryptanalysts used cillies, in conjunction with the different turnover points for rotors I to V, to find which rotors could, and which could not, be in any given slot in the machine, which often reduced the number of rotor orders to be tested to six or under – a very considerable saving. The information derived from cillies about message keys, for example the use of keyboard sequences such as QWE or PAW, also provided the cryptanalysts with up to five three-letter cribs for a five-part message.
Figure AIV.1 Part of Imaginary Blist
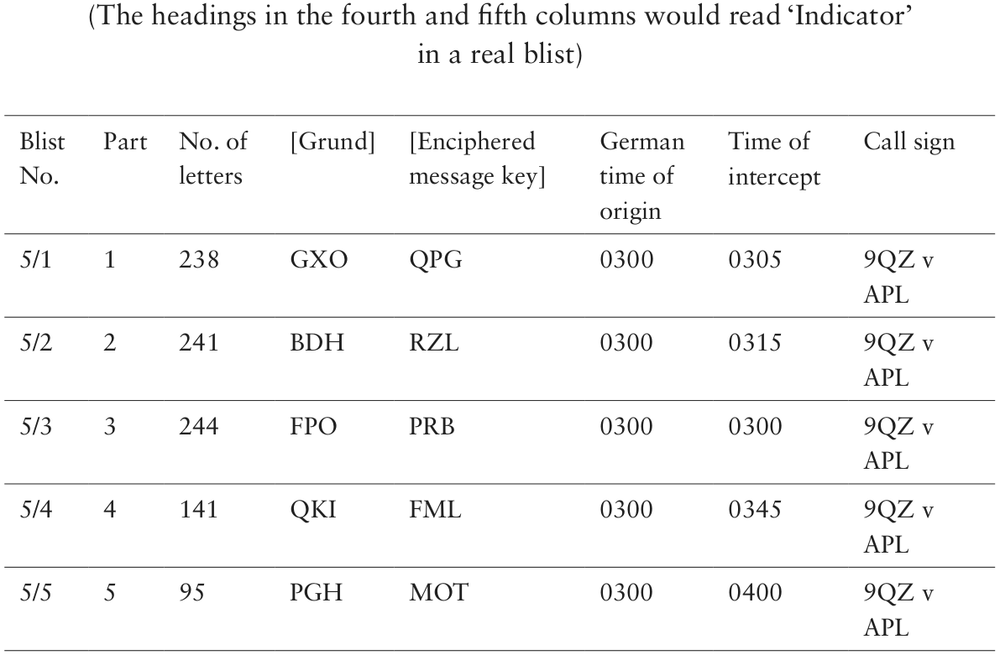
Figure AIV.l sets out part of an imaginary blist for a Luftwaffe cipher net. Let’s test the first message part for a cilli by subtracting
its length, 238 (9×26+4) from BDH, the basic setting of message part 5/2. The following starting points (message keys) for the message are therefore possible: BUD, BTD, ATD,
ASD
. Similarly, in message 2, counting back 241 (9×26+7) letters from FPO gives
FGH
, FFH, EFH or EEH, as potential message keys, after allowing for various rotor turnover positions. In message 3, subtracting 244 (9×26+10) letters from QKI gives QBY,
QAY
, PAY or PZY, while in message 4, we get PBW,
PAW
, OAW or OZW. Since we have four clear keyboard sequences here (italicized – see Figure AIV.2), it is almost certain that we do indeed have a cilli.
In message 5/2, counting back four letters from H (in the fast, right-hand slot) gives D. Counting back nine letters from D in the middle position gives U. However, the right-hand rotor may have passed through a turnover point between D and H – we don’t know until we can limit the choice of rotors – which would result in the middle rotor moving ten times, so starting at T. The middle rotor may have advanced the slow rotor once, depending on the position of its turnover, so the slow rotor must have been set at B or A. If it started at A, the middle rotor has made an extra movement, making ten or eleven, and its starting position S or T. Since the
Luftwaffe
Enigma operators often use keyboard sequences, such as ‘horizontals’ like DFG or UZT (see Figure AIV.2), or ‘diagonals’ like WAP or RDX, the message key is almost certainly ASD.
Figure AIV.2
Wehrmacht
Enigma’s key board
QWERTZUIO
ASDFGHJK
PYXCVBNML
Figure AIV.3 Rotor turnover positions
| | Rotor | I | II | III | IV | V |
| | Turnover position | Q/R | E/F | V/W | J/K | Z/A |
With message key ASD, and finishing position BDH, the notch on the middle rotor must be between S and D. Only rotors III and V have turnover notches between those letters (see Figure AIV.3). We have found ten of the eleven movements by the middle rotor from S to D. The fast rotor’s movements from D to H must have caused the middle rotor to advance, making its total eleven. The fast rotor’s notch is therefore between D and H, and it can only be II. The possible rotor orders to test when finding the
Stecker
are (5–2), III/V, II: six permutations instead of sixty, a very considerable reduction indeed. We can also use the message keys in the remaining parts of the message to obtain short cribs. In message 5/2, we have FGH, a horizontal keyboard sequence, in message 5/3, QAY, a diagonal, and in 5/4, PAW, another diagonal. The cilli has therefore also provided us with four three-letter cribs: ASD, FGH, QAY and PAW plain-text, giving QPG, RZL, PRB and FML as cipher text. We are well on the way to a solution by hand so long as the
Ringstellungen
have been found by a Herivel tip. And if bombes are available, the reduction in the number of rotor orders will save a great deal of scarce bombe time, just as in Banburismus.
Cillies seem very obvious once they are pointed out, but the German authorities cannot have realized for many years that they were providing so much useful information, including cribs, in messages. However, in August 1944, the
Heer
introduced a procedure requiring operators to generate and use fully random lists of message keys. From 15 September 1944, the same order required operators sending long messages to advance the slow rotor by at least five places between the 70th and 130th letters, and to indicate the change by the letters ‘CY’. The two procedures prevented Hut 6 from tracing cillies, but they had been introduced much too late in the day. Had the
Luftwaffe
, in particular, used them from 1940 onwards, the story of Hut 6 would have been very different indeed.
ENCIPHERING BY JN-25
This describes the JN-25 system in its most usual form. Variations did occur, for example in the nature of scanning and in the numbers of lines and columns on the additive page. As with subtractors generally, there were three steps.
First a codebook is used to transform the message into a series of codegroups, each of a set number of figures or letters. JN-25 codegroups had five digits, and the feature that the sum of the digits was divisible by three (colloquially, they scanned). This was to detect errors in transmission or recording, but incompletely so since one garble in three will scan.
Most codegroups represented one word. To cut down repetition, very frequently used words like
maru
(ship) were given numerous codegroups. Some codegroups, on the other hand, represented whole phrases like
sa no go to ki
(as follows) or ‘preparing to leave port’. Others represented numbers, or Western alphabet letters or Japanese kana needed to spell out placenames and words that did not have their own codegroup. Like translation dictionaries, the codebook was indexed in both directions to be used either way round.
Next comes the enciphering table, many pages each with 10 rows and 10 columns of random 5-digit numbers to be used as additives. For each message a starting-point is chosen, from which the necessary number of consecutive additives is taken and written out above the message codegroups. Cipher clerks were instructed to spread their chosen starting-points evenly across the whole of the tables, but human weakness led them to start most often at the left end of a line, or even at the top-left corner of a page. This gave the cryptanalysts more and deeper depths than if the instructions had been rigorously followed.
The chosen starting-point, designated by its page, line and column, had to be conveyed to the cipher clerk at the receiving end. This was done by an indicator system, a smaller cipher within the main cipher, which the cryptanalysts also had to solve from time to time.
Finally each codegroup and its enciphering additive were added together by non-carrying addition (that is, 28+17 = 35, not 45) to produce the enciphered groups then transmitted as the enciphered message. At the receiving end the procedure was reversed. With the starting-point identified and the additive groups taken from the table, each was subtracted (non-carrying) from its corresponding enciphered group to return the message to codegroup form. The codebook then finally transformed it back into language.
An illustration:
| | Codegroups | 38664 | 34131 | 70635 | |
| | Additives | 28057 | 68035 | 60457 | |
| | Enciphered groups | 56611 | 92166 | 30082 | |

