SAS Urban Survival Handbook (66 page)
Read SAS Urban Survival Handbook Online
Authors: John Wiseman
Tags: #Health & Fitness, #Reference, #Survival, #Fiction, #Safety, #Self-Help, #Personal & Practical Guides, #General, #Survival Skills

Many people, quite naturally, choose codes with personal associations—the names of their children in birth order, the name of a favourite holiday resort, their favourite food. However, a saboteur could research such personal information to try to arrive at the correct codes. Using a series of figures linked with telephone numbers, social security numbers or birth dates is risky for the same reason.
In selecting codes, mixtures of letters and figures are preferable—to produce a wider range of variables. The longer the code the more numerous the variables become.
REMEMBER
When unattended, secret and sensitive disks should be locked in a safe or vault. Simple storage boxes could be smashed open or taken away and broken into later. Information on disks could not only be read, but also altered. Fortunately the time taken and expense involved in breaking codes and operating surveillance can be prohibitive.
Computer viruses
Viruses that infect computers or computer networks behave, in some ways, like real diseases. A computer network could suddenly become very ‘sick’. Most are stupid, but often devastating, practical jokes—others may constitute serious sabotage. Only when a program begins to go wrong does the ‘sickness’ become apparent.
Viruses are ‘caught’ when a program containing the virus is fed into the system. Once it has entered, it can affect other programs, disks, terminals and networks. Viruses can also be transmitted down telephone lines.
Screening for viruses
Fortunately, screening programs are now available which can check every new disk for viruses. These screening programs should be used at the beginning and end of every work period (at least) on every terminal and before and after ANY new disk is inserted.
Checks on disks from outside sources should be made at a terminal which is not linked to others and not used for other work. In this way a virus can only be caught by that terminal and can be ‘cured’ or erased on that terminal. Modems (phone links) should NOT allow access to a whole network—a terminal should be set aside to receive incoming transmissions so that outside ‘infection’ can be contained.
Anti-viral ‘disinfectant’ programs are available to ‘cure’ most known viruses.
Funny but deadly
Most viruses are created by fairly clever people with ‘nothing better to do’, although there may be cases of revenge by unhappy employees. One of the first known was a ‘time bomb’—viruses are often designed to do their work at a prescribed time, or to be triggered when certain conditions occur. The time bomb involved a ‘Happy Birthday’ greeting to one of the largest computer corporations on a special anniversary. The fullscreen greeting popped up on VDUs all over the world.
Viruses can cause extremely odd problems—and may not be spotted until it’s too late. Some only ‘mess up’ programs or systems—others are more ‘imaginative’. It’s impossible to predict what the next joker may dream up but—to give you an idea—here are some examples of real viruses:
- ◑ The cursor dies and falls to the bottom of the screen or becomes ‘bouncy’ and impossible to control with a mouse.
- ◑ One figure in a huge column of figures spontaneously changes—every nine becomes a four, for example.
- ◑ A picture appears across the screen—one famous example was a very rude drawing of a naked woman. While the operator stares in surprise the entire memory of the hard disk in his/her terminal is erased.
- ◑ Obscene words appear in the middle of innocent documents, often triggered by common word combinations.
- ◑ Obscene insults to the user flash up on the screen. Perhaps the weirdest aspect of viruses is that some have been known to lie dormant for long periods of time, to mutate or even combine with other viruses to produce new ones. Strict screening procedures have helped to reduce the spread—but enormous damage has been done.
VEHICLES
 Cars should always be securely locked when parked. Choose a fairly busy location – under a streetlamp at night, if you can’t park in a garage or off the road. Make sure that all windows and sunroofs are secured. In
Cars should always be securely locked when parked. Choose a fairly busy location – under a streetlamp at night, if you can’t park in a garage or off the road. Make sure that all windows and sunroofs are secured. In
Britain alone, a car is stolen every two minutes!
A variety of devices is available to prevent the car from being driven, even if a thief has a key that fits the ignition or bypasses the ignition. There are simple restraining bars to lock the steering wheel to a pedal, or immobilize the gear stick. Increasingly, locking devices may be built into the car itself.
Car alarms, like those for buildings, operate in a variety of ways. Some use infra-red beams to detect any movement within the car. Others are vibration detectors which respond to movement of the car itself—some are so sensitive that even touching the car can set them off. Careful adjustment is necessary if there are not to be repeated false alarms.
Radios
NEVER leave valuables in a car—or if there is no option then make sure that they are locked out of sight—don’t tempt thieves! Car stereo systems are a favourite of thieves. Some car manufacturers are coding digitally-tuned radios to match the individual car. An experienced thief should recognize this type and leave it alone. One drawback that was found with this system is that they have to be returned to the manufacturer to be reset, if your battery ever runs down.
Other radios are made to slide into and out of the fascia board. They can be removed easily so that you take them with you. If you forget or don’t bother, it is just as easy for a thief to slip the radio out! DON’T hide it under the seat—that is the first place a thief will look! Take it with you. The drawback is that you may simply lose the radio!
Motorcycles/bicycles
Motorcycles have steering locks to prevent them being ridden away by thieves but that will not deter professionals who may load them on a lorry. Chain them to railings, a lamppost or other fixture. A cable alarm system can be used which will be activated if it is severed.
Bicycles are particularly vunerable to theft. The whole bike needs securing—thieves commonly steal individual bicycle parts. An expensive front wheel should have a quick-release mechanism. Detach it, run the security cable or chain through it, through the back wheel and the frame and around a fixed post. Even this, however, will not deter a determined thief.
Work & play
Many jobs involve hazardous processes or chemicals, but
even working in an office may pose severe risks. Leisure activities, too, carry a level of danger – this may be part of the thrill of many sports, but serious injuries are common.
THE WORKPLACE
Hazardous chemicals • Diseases/disorders • Physical damage • Noise • Radiation risks
• Work posture • The unhealthy office • ′Sick′ buildings • Legionnaire’s disease • Humidifier fever
• The public • Working outside
LEISURE
Television • Music • Barbecues • Spectators • Angling • Playgrounds • Radio-controlled models
• Fireworks • On the town
SPORT
Strength • Stamina • Suppleness • Warming up/cooling down • Women and sport
• Types of injury • Clothing • Sport by sport
THE WORKPLACE
 Although factories, shops and business premises may be regulated by laws concerning work conditions and safety measures, it is the workforce itself which must see that these laws are implemented. The people who
Although factories, shops and business premises may be regulated by laws concerning work conditions and safety measures, it is the workforce itself which must see that these laws are implemented. The people who
actually do the jobs should be most able to see when laws are ignored, and to recognize when safety measures are inadequate. Discover, through your union or staff organization, what regulations apply and see that they are followed. An occupation should NOT involve you risking your life or your long-term health.
PLEASE NOTE
It is not possible to give full details of EVERY type of work hazard for EVERY occupation. The information given here is designed to highlight types of hazard, some of which may be quite unusual. Think about YOUR job and its risks. Are you safe?
Fire
The provision of appropriate smoke detectors, alarms, sprinkler systems, fire-fighting equipment, fire exits and escape routes is VITAL. Use fire-fighting equipment only if you have been trained and you know what kind of fire it is appropriate for. Know the location of fire exits. Fire drills should be held regularly and taken seriously. Responsibility for helping any disabled or injured colleagues, or anyone else who might need special help, should be assigned and such assistance practised (see FIRE!:
Equipment & drills
).

WARNING
Don’t increase fire risks! NEVER let piles of inflammable waste or scrap build up in the workplace. ALWAYS clear up spills of oil, fuels and solvents.
HAZARDOUS CHEMICALS
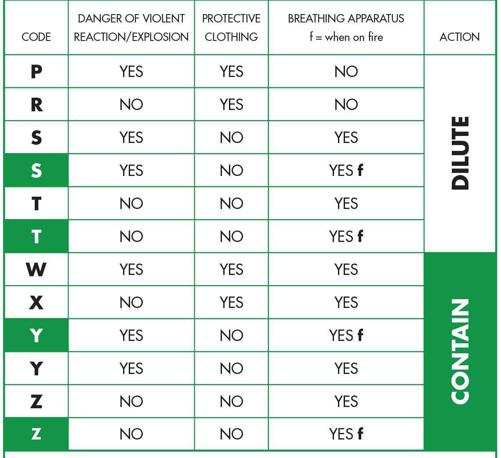
 Where hazardous chemicals and other potentially-dangerous materials are stored or are used, ‘hazchem’ symbols should be displayed. These indicate the nature of the danger to the emergency services and give them guidelines for dealing with it. Unfortunately the codes are not internationally identical.
Where hazardous chemicals and other potentially-dangerous materials are stored or are used, ‘hazchem’ symbols should be displayed. These indicate the nature of the danger to the emergency services and give them guidelines for dealing with it. Unfortunately the codes are not internationally identical.
HAZCHEM CODES