Windows Server 2008 R2 Unleashed (36 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

FIGURE 4.11
Applying a PSO to a group.
3. When prompted that stopping AD DS will stop other associated services such as
DNS, DFS, Kerberos, and Intersite Messaging, choose Yes to continue.
4. To restart AD DS, right-click the AD DS service and choose Start. Start the Intersite
Messaging Service and Kerberos Key Distribution Center service as well.
Implementing Multiple Password Policies per Domain
Another Windows Server 2008 addition to AD DS is the ability to implement granular
password policies across a single domain. Previously, this was only an option with third-
party password change utilities installed on the domain controllers in a forest. With
138
CHAPTER 4
Active Directory Domain Services Primer
Windows Server 2008 or Windows Server 2008 R2, administrators can define which users
have more complex password policies, and which will be able to use more lenient policies.
There are a few key points to this technology that must be understood before implement-
ing it. These points are listed as follows:
. Domain mode must be set to Windows Server 2008 or Windows Server 2008 R2
level, which means that all DCs in the domain must be running Windows Server
2008 R2 or RTM.
. Fine-grained password policies always win over a domain password policy.
. Password policies can be applied to groups, but they must be global security groups.
. Fine-grained password policies applied to a user always win over settings applied
to a group.
. The Password Settings Objects (PSOs) are stored in the Password Settings Container
in AD (that is, CN=Password Settings
Container,CN=System,DC=companyabc,DC=com).
. Only one set of password policies can apply to a user. If multiple password policies
are applied, the policy with the lower number precedence wins.
ptg
To create a custom password policy for a specific user, a Password Settings Object (PSO)
must be created using the ADSIEdit tool, which is used for low-level changes to AD DS or
AD LDS directory objects and attributes.
CAUTION
ADSIEdit is a very powerful, low-level directory editor, and great care should be taken
when using it. Be extremely cautious using the editor, especially when deleting objects,
as ADSIEdit could easily delete entire portions of an AD tree with a single keystroke if
care is not taken.
The version of ADSIEdit included with Windows Server 2008 RTM/R2 provides for a crude
wizard that allows for PSOs to be created. The wizard automates the creation of a PSO, and
allows for specific attributes to be set on the PSO that are related to password policies.
Table 4.1 displays the attributes that are prompted for creation by the wizard. All attrib-
utes in this table must be entered in the proper format for a PSO to be created. Note that
only the final attribute in this list msDS-PSOAppliesTo is not prompted by the wizard, and
must be entered in manually.
Outlining AD DS Changes in Windows Server 2008 R2
139
TABLE 4.1
PSO Attributes
Attribute
Description
Sample Value
Cn
The unique name of the password
PasswordPolicyforAdmins
policy.
msDS-PasswordSettings
The priority of the policy. Lower
20
Precedence
number “wins.” Leave space on both
sides of the number to reprioritize if
necessary.
msDS-PasswordReversible
The policy used for specific circum-
FALSE
EncryptionEnabled
stances where a user’s password
needs to be able to be decrypted.
Normally set to False.
4
msDS-PasswordHistory
The number of passwords “remem-
10
Length
bered” by the system.
msDS-PasswordComplexity
The policy that sets whether or not
TRUE
Enabled
password complexity is enabled.
Password complexity enforces whether
users should be forced to include a
ptg
combination of numbers, uppercase
letters, lowercase letters, and special
characters as part of their password.
Enabling complexity forces them to
include at least three of the four types
in their passwords.
msDS-MinimumPassword
The policy setting that enforces the
8
Length
minimum password character length.
msDS-MinimumPasswordAge
The minimum number of days that
3:00:00:00
must be waited before resetting the
password to something different. This
disallows users from simply “cycling
through” password changes to keep
the same password. Expressed in a
format of
Days:Hours:Minutes:Seconds. For
example, 3:00:00:00 equals 3 days.
msDS-MaximumPasswordAge
The maximum number of days that a
60:00:00:00
password is valid for. Expressed in a
format of
Days:Hours:Minutes:Seconds.
msDS-LockoutThreshold
The number of invalid password
5
attempts that can be made before
locking out the account.
140
CHAPTER 4
Active Directory Domain Services Primer
TABLE 4.1
T
PSO Attributes
Attribute
Description
Sample Value
Attribute
Description
Sample Value
msDS-LockoutObservation
The length of time (expressed in
0:00:10:00
Window
Days:Hours:Minutes:Seconds format)
before the invalid password attempt
counter is reset. Cannot exceed the
msDS-LockoutDuration value.
msDS-LockoutDuration
The length of time (expressed in
0:00:15:00
Days:Hours:Minutes:Seconds format)
an account remains locked out.
msDS-PSOAppliesTo
The user or group of users to which
CN=Admins, OU=Admins,
the PSO applies. Note that this field is OU=Resources,
not displayed as part of the default
DC=companyabc,
wizard; you must click the More
DC=com
Attributes button at the end of the
wizard and enter the distinguished
name (DN) of the group or user object.
Enter the group using its full DN. Read
the previous sections of this chapter
ptg
for more information on how to format
a DN. In this example, the policy will
apply to the Global Security named
Admins in the Resources—Admins OU
in companyabc.com.
To create a new PSO, open ADSIEdit from the Administrative Tools menu and point it to
the fully qualified domain name (FQDN) of the domain where the PSO will be created.
After ADSIEdit has been invoked, perform the following steps to create a PSO:
1. Under the container for the domain, navigate to CN=System, CN=Password
Settings Container.
2. Right-click on the CN=Password Settings Container, and choose New, Object.
3. Select msDS-PasswordSettings, and click Next to continue.
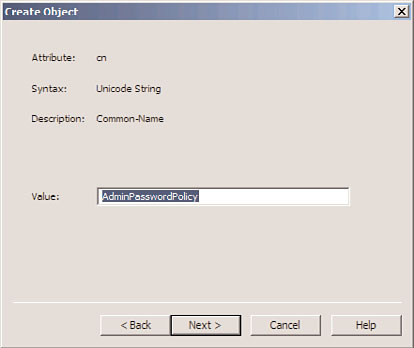
4. From the Create Object dialog box, shown in Figure 4.12, enter in the attributes,
using Table 4.1 as a guide.
5. When on the final screen of the wizard, click the More Attributes button.
6. Click the Select a Property to View drop-down list arrow, and then select msDS-
PSOAppliesTo.
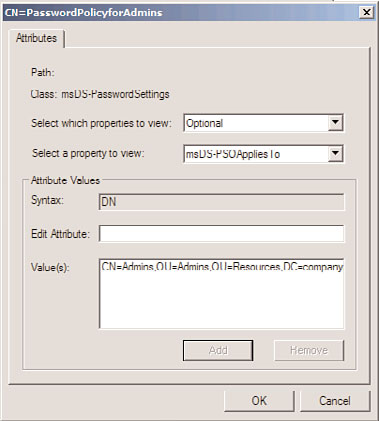
7. In the Edit Attribute field, enter the DN of the group or user to which the PSO will
apply. Be sure to click the Add button, or the setting will not be applied. The value
should be displayed, similar to what is shown in Figure 4.13.
8. Click OK and then click Finish.
Outlining AD DS Changes in Windows Server 2008 R2
141
4
FIGURE 4.12
Creating a PSO.
ptg
FIGURE 4.13
Applying a PSO to a group.
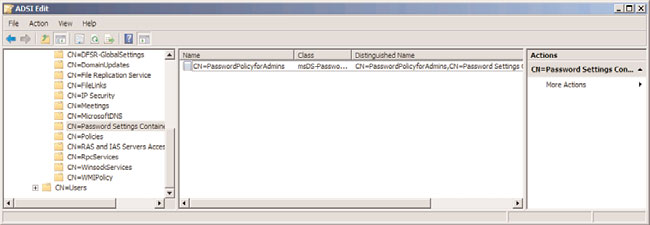
After creation, the PSO policy will appear in the details pane, as shown in Figure 4.14. Any
of the attributes listed in Table 4.1 can be subsequently modified using ADSIEdit by right-
clicking the individual PSO and choosing Properties. This includes changing the scope of
which users the policy applies to.
142
CHAPTER 4
Active Directory Domain Services Primer
FIGURE 4.14
Viewing the PSO object.
Auditing Changes Made to AD Objects
Another important change to Active Directory that can be enabled in a Windows Server
2008 or Windows Server 2008 R2 functional domain is the concept of auditing changes
made to Active Directory objects. Previously, it was difficult to tell when changes were
made, and AD-specific auditing logs were not available. Windows Server 2008 RTM/R2
allows administrators to be able to determine when AD objects were modified, moved,
or deleted.
ptg
To enable AD object auditing on a Windows Server 2008 RTM/R2 domain controller,
perform the following steps:
1. From a member server or domain controller, click Start, All Programs, Administrative
Tools, Group Policy Management.
2. Navigate to
Domain Controllers Policy.
3. Click Edit.
4. In the GPO window, navigate to Computer Configuration, Policies, Windows
Settings, Security Settings, Local Policies, Audit Policy.
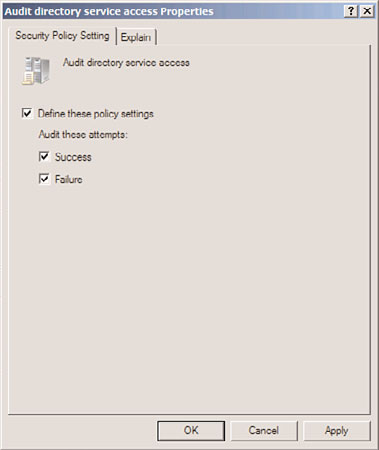
5. Under the Audit Policy setting, right-click on Audit Directory Service Access, and
click Properties.
6. Check the Define These Policy Settings check box, and then check the Success and
Failure check boxes, as shown in Figure 4.15.
7. Click OK to save the settings.
Global AD DS auditing on all DCs will subsequently be turned on. Audit event IDs will be
displayed as Event ID 5136, 5137, 5138, 5139, or 5141, depending on if the operation is a
modify, create, undelete, move, or delete respectively.