Windows Server 2008 R2 Unleashed (11 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

server-to-server session communications, an administrator can configure a group of
servers, manage a group of servers, and reboot a group of servers all from a series of
PowerShell commands.
All future server products released from Microsoft will have the PowerShell foundation
built in to the core Windows Server 2008 R2 operating system, thus making it easier for
products running on Windows Server 2008 R2 to use the same administrative scripting
language. PowerShell is covered in detail in Chapter 21, “Automating Tasks Using
PowerShell Scripting.”
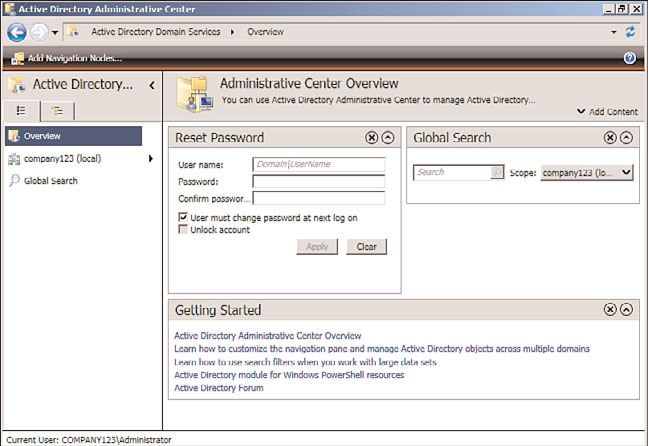
Active Directory Administrative Center
New to Windows Server 2008 R2 and built on PowerShell v2.0, the Active Directory
Administrative Center is a customizable console that an organization can create for
specific administrators in the organization. As an example, an organization might have an
administrator who only needs to reset passwords, or another administrator who only
needs or manage print queues. Rather than giving the administrator access to the full
Active Directory Users and Computers or Print Management consoles, an Active Directory
Administrative console can be created with just a task or two specific to the administra-
ptg
tor’s responsibilities.
The console is built on PowerShell, so underlying the GUI are simple PowerShell scripts.
Anything that can be done in PowerShell on a Windows Server 2008 R2 server can be
front-ended by the administration console. An example of the console is shown in Figure
1.6, and the tool is covered in detail in Chapter 18, “Windows Server 2008 R2
Administration.”
Increased Support for Standards
The release of Windows Server 2008 introduced several industry standards built in to the
Windows operating system that have since been updated in Windows Server 2008 R2.
These changes continue a trend of the Windows operating system supporting industry
standards rather than proprietary Microsoft standards. One of the key standards built in to
Windows Server 2008 and Windows Server 2008 R2 is IPv6.
Internet Protocol version 6 (or IPv6) is the future Internet standard for TCP/IP addressing.
Most organizations support Internet Protocol version 4 (or IPv4). Due to the Internet
numbering scheme running out of address space in its current implementation of address-
ing, Internet communications of the future need to support IPv6, which provides a more
robust address space.
Additionally, IPv6 supports new standards in dynamic addressing and Internet Protocol
Security (IPSec). Part of IPv6 is to have support for the current IPv4 standards so that dual
addressing is possible. With Windows Server 2008 R2 supporting IPv6, an organization can
choose to implement a dual IPv6 and IPv4 standard to prepare for Internet communica-
tions support in the future. IPv6 is covered in detail in Chapter 10.
20
CHAPTER 1
Windows Server 2008 R2 Technology Primer
FIGURE 1.6
Active Directory Administrative Center.
ptg
As noted earlier in this chapter, Active Directory in Windows Server 2008 R2 hasn’t
changed to the point where organizations with solid Active Directory structures have to
make changes to their directory environment. Forests, domains, sites, organizational units,
groups, and users all remain the same. There are several improvements made in Active
Directory and the breadth of functionality provided by directory services in Windows
Server 2008 R2.
The changes made in Active Directory are captured in the name changes of directory
services as well as the introduction of a Read-Only Domain Controller service introduced
in Windows Server 2008.
Renaming Active Directory to Active Directory Domain Services
In Windows Server 2008, Active Directory was renamed to Active Directory Domain
Services (AD DS), and Windows Server 2008 R2 continues with that new name. Active
Directory Domain Services refers to what used to be just called Active Directory with the
same tools, architectural design, and structure that Microsoft introduced with Windows
2000 and Windows 2003.
The designation of Domain Services identifies this directory as the service that provides
authentication and policy management internal to an organization where an organiza-
tion’s internal domain controls network services.
Changes in Active Directory
21
For the first time, AD DS can be stopped and started as any other true service. This facili-
tates AD DS maintenance without having to restart the domain controller in Directory
1
Services Restore Mode.
Renaming Active Directory in Application Mode to Active Directory
Lightweight Directory Service
Another name change in the directory services components with Windows Server 2008
from Microsoft is the renaming of Active Directory in Application (ADAM) to Active
Directory Lightweight Directory Services (AD LDS). ADAM has been a downloadable add-
in to Windows 2003 Active Directory that provides a directory typically used in organiza-
tions for nonemployees who need access to network services. Rather than putting
nonemployees into the Active Directory, these individuals—such as contractors, temporary
workers, or even external contacts, such as outside legal counsel, marketing firms, and so
on—have been put in ADAM and given rights to access network resources such as
SharePoint file libraries, extranet content, or web services.
AD LDS is identical to ADAM in its functionality, and provides an organization with
options for enabling or sharing resources with individuals outside of the organizational
structure. With the name change, organizations that didn’t quite know what ADAM was
ptg
before have begun to leverage the Lightweight Directory Services function of Active
Directory for more than resource sharing but also for a lookup directory resource for
clients, patients, membership directories, and so on. Active Directory Lightweight
Directory Services is covered in detail in Chapter 8, “Creating Federated Forests and
Lightweight Directories.”
Expansion of the Active Directory Federation Services
That leads to the third Active Directory service called Active Directory Federation Services,
or AD FS. Active Directory Federation Services was introduced with Windows 2003 R2
edition and continues to provide the linking, or federation, between multiple Active
Directory forests, or now with Windows Server 2008 R2 Active Directory Federation
Services, the ability to federate between multiple Active Directory Domain Services systems.
Effectively, for organizations that want to share information between Active Directory
Domain Services environments, two or more AD DS systems can be connected together to
share information. This has been used by organizations that have multiple subsidiaries
with their own Active Directory implemented to exchange directory information between
the two organizations. And AD FS has been used by business trading partners (suppliers
and distributors) to interlink directories together to be able to have groups of users in both
organizations easily share information, freely communicate, and easily collaborate
between the two organizations.
Active Directory Federation Services is covered in detail in Chapter 8.
22
CHAPTER 1
Windows Server 2008 R2 Technology Primer
Introducing the Read-Only Domain Controller
Another change in Active Directory in Windows Server 2008 that was continued in
Windows 2008 R2 was the addition of a Read-Only Domain Controller, or RODC. The
RODC is just like a global catalog server in Active Directory used to authenticate users and
as a resource to look up objects in the directory; however, instead of being a read/write
copy of the directory, an RODC only maintains a read-only copy of Active Directory and
forwards all write and authentication requests to a read/write domain controller.
RODCs can also be configured to cache specified logon credentials. Cached credentials
speed up authentication requests for the specified users. The cached credentials are
stored in cache on the RODC system, not every object in the entire global catalog. If the
RODC is shut down or powered off, the cache on the RODC is flushed, and the objects
in cache are no longer available until the RODC connects back to a global catalog server
on the network.
The RODC is a huge advancement in the area of security being that a RODC cannot be
compromised in the same manner that a global catalog server can be in the event of a
physical theft of a domain server. Organizations that require the functionality of a global
catalog server for user authentication that have the global catalog server in an area that is
not completely secure, such as in a remote office, in a branch office location, or even in a
retail store outlet, can instead put a RODC in the remote location.
ptg
Windows Server 2008 R2 Benefits for
Windows Server 2008 R2 provides several new benefits that help organizations better
administer their networking environment. These new features provide better file and data
management, better performance monitoring and reliability tracking tools to identify
system problems and proactively address issues, a new image deployment tool, and a
whole new set of Group Policy Objects that help administrators better manage users,
computers, and other Active Directory objects.
Improvements in the Group Policy Management
Windows Server 2008 R2 introduces over 1,000 new Group Policy Objects specific to
Windows Server 2008 R2 and Windows 7, along with several new components that
expand on the core capabilities of Group Policy management that have been part of
Windows 2000/2003 Active Directory. The basic functions of Group Policy haven’t
changed, so the Group Policy Object Editor (gpedit) and the Group Policy Management
Console (GPMC) are the same, but with more options and settings available.
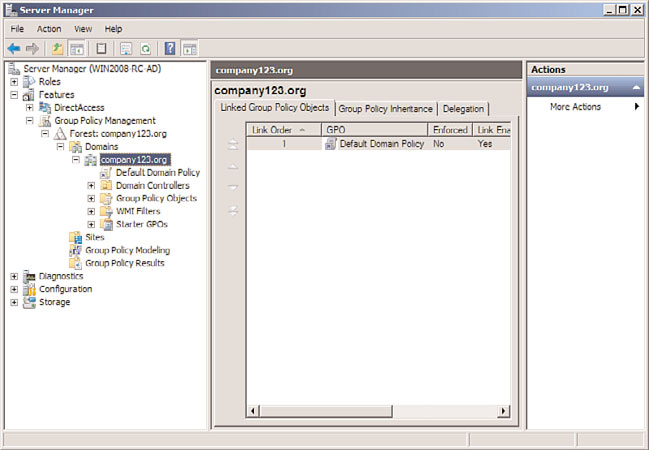
As mentioned earlier, the Group Policy Management Console can either be run as a sepa-
rate MMC tool, or it can be launched off the Features branch of the Server Manager
console tree, as shown in Figure 1.7. Group policies in Windows Server 2008 R2 provide
more granular management of local machines, specifically having policies that push down
to a client that are different for administrator and non-administrator users.
Windows Server 2008 R2 Benefits for Administration
23
1
FIGURE 1.7
Group Policy Management Console.
ptg
Additionally, applications can now query or register with a network location awareness
service within Group Policy management, which provides the identity where a user or
computer object resides. As an example, a policy can be written that allows users to have
access to applications and files if they are on a local network segment, but blocks users
from accessing the same content when they are on a remote segment for security and
privacy reasons. This addition to group policies adds a third dimension to policies so that
now administrators can not only define who and what someone has access to, but also
limit their access based on where they are.
Group policies are covered in detail in Chapter 27, “Group Policy Management for
Network Clients,” as well as in Chapter 19, “Windows Server 2008 R2 Group Policies and
