Liars and Outliers (19 page)
Read Liars and Outliers Online
Authors: Bruce Schneier

Let's put this all together. Think about an employee traveling for company business on an expense account. He can either live frugally, or enjoy the most expensive hotels, restaurants, and so on. It's a societal dilemma:
Here are some more societal dilemmas, and corresponding security systems that act as societal pressures.
- Gridlock
. Security measures include traffic cops to keep cars moving, specially striped intersections to demarcate off-limits areas, and cameras to assist enforcement at gridlock-prone intersections. - Vaccines
. There is ongoing research on how to rebuild public
confidence in vaccines
and reduce defection. Tactics could include ad campaigns and other types of marketing. Also, inhalable vaccines make it easier to cooperate. - Cheating at games
. It's more fun for the group if everyone plays fairly, but it's sometimes more fun for the individual to cheat and win. To help combat cheating, the
new version of Monopoly
comes with an electronic gadget that keeps track of everyone's money and makes sure they go to the right square—no cheating.
| Societal Dilemma: Corporate expenses. | |
| Society: The corporation. | |
| Group interest: Minimize corporate expenses. | Competing interest: More enjoyable corporate travel. |
| Group norm: Spend the corporation's money frugally. | Corresponding defection: Spend a lot on hotel, meals, and so on. |
| To encourage people to act in the group interest, the society implements a variety of trust mechanisms. Moral: A company-wide belief that frivolous expenses are tantamount to stealing. Reputational: Praising people who save the company money. Publicly chastising people who spend lavishly. Institutional: Corporate travel policies, including per diem systems and daily spending limits. Security: E-mail reminders that people should be parsimonious with the company's money (enhances moral pressure). Requiring employees to submit for approval estimates of how much they'll spend beforehand, and making it difficult to get additional expenses reimbursed (enhances both moral and reputational pressure). Putting everyone's travel expenses on a website that everyone in the company can see (enhances reputational pressure). Requiring booking of airfare and hotels through a dedicated travel agent, who enforces the corporate policies (enhances institutional pressure). Auditing of travel expenses, with overspenders being forced to reimburse the company (enhances institutional pressure). |
A lot of those might not feel like security systems, but they are. The breadth of security systems is vast. This chart—from criminal justice professor Ronald V. Clarke—illustrates just how diverse security can be.
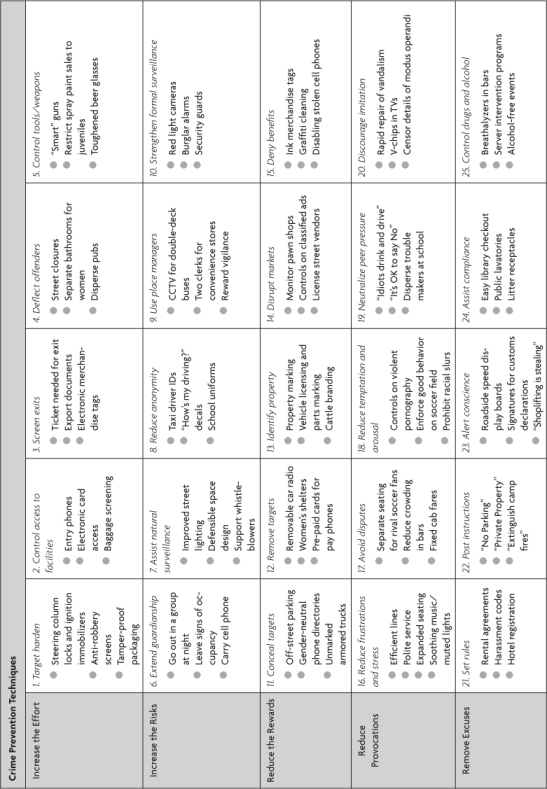
In fact, one way to look at societal pressures is that
everything
I've written about in these past four chapters is a security system. Morals act as a pre-emptive intervention system. Reputation is a detection and response system; so are laws and sanctions. Taxes and incentives are interventions. And so on. While that may be true—and as a security guy that's really how I think of it all—it's more useful to think of security as its own thing.
I'm not going to talk more about specific security systems, both because such discussions can quickly get very technical, and because there are shelves full of books already written on the subject.

The use of performance-enhancing drugs in professional sports is a societal dilemma, and a good example of how security systems fail as a societal pressure.
2
| Societal Dilemma: Doping in professional sports. | |
| Society: All the athletes in the sport. | |
| Group interest: A safe and fair sport. | Competing interest: Winning and making a lot of money. |
| Group norm: Don't take performance-enhancing drugs. | Corresponding defection: Take performance-enhancing drugs. |
| To encourage people to act in the group interest, the society implements a variety of trust mechanisms. Moral: Guilt at not winning fair and square. Reminders that athletes are role models, and appeals to “think of the children.” Reputational: Keep fans and endorsements by maintaining the reputation of a fair player. Institutional: Bans on performance-enhancing drugs. Security: Drug testing for specific performance-enhancing drugs. |
That's the idea, at least.
3
It turns out that
enforcing anti-doping
rules is very difficult. The problem is while the intent of the rules is to ban performance-enhancing drugs in general, the temptation to ignore the group interest and take these drugs is enormous. Here's a quote from professional cyclist
Alex Zülle
:
I've been in this business for a long time. I know what goes on. And not just me, everyone knows. The riders, the team leaders, the organizers, the officials, the journalists. As a rider you feel tied into this system. It's like being on the highway. The law says there's a speed limit of 65, but everyone is driving 70 or faster. Why should I be the one who obeys the speed limit? So I had two alternatives: either fit in and go along with the others or go back to being a house painter. And who in my situation would have done that?
Before the sport started paying attention, distance cyclists used stimulants such as caffeine, cocaine, nitroglycerine, amphetamines, and painkillers to improve their endurance. It's a classic arms race—everyone had to partake in order to keep up—and many athletes suffered catastrophic health effects from long-term use. Morals and reputation aren't going to work in situations like this, and the only effective measures are institutional rules enforced by security systems: tests for specific drugs. France passed the first anti-doping laws in 1965; testers found that
almost a third
of the participants in the Tour de France the next year tested positive for amphetamines. Over the decades, each new potentially performance-enhancing substance was countered with a ban and then a test.
4
Blacklists now encompass hundreds of substances.
Yet inconsistencies among various regulatory bodies' blacklists have led to the occasional sanction against athletes who
never intended
to break the rules.
5
At the 2000 Olympics, Romanian gymnast Andreea Râducan was
stripped of her gold medal
because she tested positive for pseudoephedrine; she had taken two pills of an over-the-counter cold medicine prescribed by her team doctor.
Security systems fail for several broad reasons.
They don't work as well as advertised
. Technologies are often developed and sold by companies that tout their value, even if there's no real evidence to support it. So municipalities
install security cameras
in a mistaken belief that they prevent crime, the TSA buys
full-body scanners
in a mistaken belief that they prevent terrorism, and the
military spends billions
on weapons systems like the Sgt. York air defense gun that don't work. In previous centuries, physiognomy (facial features) and phrenology (skull measurements) were both believed to be useful in identifying criminal personalities.
Attackers develop ways around the technologies
. Attackers are always trying to figure out ways around security systems, and some of them succeed. Every anti-counterfeiting measure is eventually successfully overcome by counterfeiters.
6
(Not just paper money; improvements in metallurgy result in
better slugs
.) No matter how many tax loopholes are closed, there is enough complexity in the tax code—and enough legislators willing to slip in provisions to benefit special interests—that unscrupulous companies can always find more. There are many ways to break the security of
door locks and safes
.
Major technologies change in ways that affect the security technologies
. We'll talk about this extensively in Chapter 16. The Internet has given us an endless series of lessons in previously stable systems that failed when they moved online. For example, the security measures against impersonation fraud—identity theft—that worked in the world of face-to-face meetings and telephone conversations failed completely with online commerce. Computers make paper documents easier to forge, and
fax machines
make forgeries easier still.
Electronic voting machines
are considerably less secure than their predecessors. Modern
electronics in cars
bring with them new security risks.
Networked medical devices
can be hacked. There are hundreds of examples like this.
Sometimes the technological changes have absolutely nothing to do with the societal dilemma being secured. Between the ubiquity of keyboards and the tendency for teachers to focus on standardized tests,
cursive is not being taught
as much in schools. The result is that signatures are more likely to be either printed text or illegible scrawls, both easier to forge.
Security systems that augment other societal pressures, opening new avenues for attack
. An example will illustrate.
In a small town, everyone knows each other, and lenders can make decisions about whom to loan money to, based on reputation (like in the movie
It's a Wonderful Life
). The system isn't perfect; there are ways for defectors to hide their reputations and cheat lenders. The real problem, though, is that the system doesn't scale. In order to enable lending on a larger scale, we enhanced reputation with technological security systems. For instance, credit reports and scores are a security-augmented reputational pressure. This system works well, and lending has exploded in our society in part because of it. But the new reputational pressure system can be attacked technologically. A defector could hack the credit bureau's database and enhance her reputation by boosting her credit score. Or she could steal someone else's reputation. All sorts of attacks that just weren't possible with a wholly personal reputational system become possible against a system that works on reputation plus a security system.
Even worse, many people don't realize that adding technological security to a reputational system makes such a difference, and continue to assume that it's a wholly reputational system. This adds to the risks. Some examples:
- Licensing is an institutional—formalized reputational—pressure system. When it is augmented with physical or electronic credentials, forging them becomes a way to attack it.
- Bank payment systems once had a combination of reputational and institutional pressure systems. Today it's primarily technological, and attackable through that technology.
- We traditionally used physical cues to assess the reputation of a business: the cleanliness of a restaurant, the impressiveness of a bank's building, and so on. Today we get a lot of those same cues from websites, where they are much easier to fake.
7
More generally, our learned abilities to
read trust signals
are continually being overtaken by technology. - Universal ID systems can make impersonation fraud more profitable, because a single stolen ID can be used in many more places. Sometimes, a
harder-to-forge ID
is even riskier, because it is that much more profitable to forge.
There's a more general change afoot. We're moving a lot of our interactions with other people from evolved social systems into deliberately created socio-technical systems. Instead of having a conversation face-to-face or voice-to-voice, we have it via text or e-mail. Instead of showing our friends our vacation pictures over drinks, we publish them on Flickr. Instead of sharing the intimacies of our life in person, we do it on Facebook. Instead of hanging out with our friends in bars or even street corners, we meet in massive multi-player games with a social component like World of Warcraft and Eve Online. This is an important change. In many of these systems, the technology fades to the background—that's the point, after all—and our brains primarily focus on the social aspects. As a result, we focus on the moral and reputational pressures endemic to the human interactions and ignore the technological part. So we forget that text conversations can be stored forever, retrieved later, and shared with other people. We forget there are people reading our Facebook comments who are not generally privy to the intimacies our life. We forget that Eve Online isn't the same as a face-to-face get-together. The technology changes how our social interactions work, but it's easy to forget that.
